Researchers at UK security firm Context have formulated an attack against the Wi-Fi connected lightbulbs, which is available to buy in the UK, that exposes credentials of the Wi-Fi network, it relies on to operate, to anyone in accessibility to one of the LED devices.
Security vulnerabilities found in the LIFX Smart light bulbs, that can be controlled by the iOS-based and Android-based devices, could allow an attacker to gain access to a “master bulb” and with the help of that they could control all connected bulbs across that network, and help them expose user network configurations.
Along with other Internet of Things (IoTs) devices, the smart bulbs are part of a rising trend in which the manufacturers enclose computing and networking capabilities to their devices so that it can be easily controlled remotely by using a smartphone, computer, and other network-connected device. LIFX ran a popular fundraising campaign in 2012 on Kickstarter, raising more than $1.3 million (£760,000) which was more than 13 times the original goal of $100,000 (£59,000).
But before delivering the smart bulbs to home consumers, the company failed to properly encrypt all data in the wireless protocols it used when enrolling new bulbs on the network. The oversight allowed the researchers to craft messages to the networked bulbs within about 30 meters, forcing them to obtain security credentials used to secure the connected Wi-Fi network.
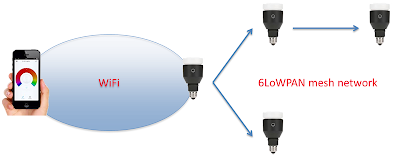
The WiFi network credentials are captured in specific packets by passing from one networked bulb to another over a mesh network powered by 6LoWPAN, a wireless specification built on top of the IEEE 802.15.4 standard. While the wifi details were encrypted by the Advanced Encryption Standard (AES), the researchers were able to obtain the secret key shared between bulbs on the network, making it easy for the attacker to decipher the payload.
"Armed with knowledge of the encryption algorithm, key, initialisation vector, and an understanding of the mesh network protocol we could then inject packets into the mesh network, capture the Wi-Fi details, and decrypt the credentials, all without any prior authentication or alerting of our presence," researchers from security consultancy Contextwrote.
“It should be noted, since this attack works on the 802.15.4 6LoWPAN wireless mesh network, an attacker would need to be within wireless range, ~30 meters, of a vulnerable LIFX bulb to perform this attack, severely limiting the practicality for exploitation on a large scale.”
LIFX quickly responded to the Context findings and has now issued a firmware update to its smart bulb firmware, which encrypted all 6LoWPAN traffic and secured the process supporting new bulbs on the network.
The company said that it was unaware of any users being affected by the security issue and released LIFX security update.
“In rare circumstances the security issue could expose network configuration details on the mesh radio, requiring a person to dismantle a bulb, reverse engineer the debug connection and firmware, then be physically present with dedicated hardware within the bounds of your WiFi network (not from the internet). Eg. Someone hiding in your garden with complex technical equipment. No LIFX users have been affected that we are aware of, and as always we recommend that all users stay up to date with the latest firmware and app updates,” the firm said in a blog post.
Reference- http://thehackernews.com/

No comments:
Post a Comment