Google has failed to provide a very important security measure in its Gmail application for iOS that left millions of its Apple device users to Man-in-the-Middle (MitM) attacks capable of monitoring encrypted email communications.
Researcher at mobile security firm Lacoon has discovered that Google’s Gmail iOS application, run on Macintosh mobile devices, does not perform what’s known as “certificate pinning” when establishing a trusted connection between the mobile applications and back-end web services, which means an attacker can view plaintext emails and steal credentials in MitM attack.
WHAT IS CERTIFICATE PINNING
Certificate Pinning is a process designed to prevent user of the application from being a victim of an attack made by spoofing the SSL certificate. Certificate pinning automatically rejects the whole connection from sites that offer bogus SSL certificates and allow only SSL connections to hosts signed with certificates stored inside the application, which ensures that you are protected against fraudulently issued certificates.
For example, if you access Google.com from your browser, it will trust the certificate if it's signed by Verisign, Digicert or any trusted Certificate Authority, but if you will connect to a Google server via an app on mobile, it will only trust the certificates signed by Google itself.
NO RESPONSE FROM GOOGLE
The company said it reported the vulnerability to Google at the end of February. Google validated the problem and told the company it was fixed, but still the security vulnerability remains exploitable in Gmail’s iOS app at the time of writing, according to the blog post published Thursday. Google has not yet responded to the issue.
“Several months after providing responsible disclosure, Google has not provided information regarding resolution and it still remains an open vulnerability,” said Michael Shaulov, CEO and co-founder of Lacoon Mobile Security. “This vulnerability leaves iPhone and iPad users at risk of a threat actor being able to view and modify encrypted communications through a Man-in-the-Middle attack.”
SEVERITY OF THE FLAW
The vulnerability allows the attackers to generate bogus certificates from configuration profiles, according to the researcher Avi Bashan of Lacoon Mobile Security, the firm that found the vulnerability.
For a successful MitM attack, it is important for an attacker to install a configuration profile on the iOS device, and this could be done by tricking users into downloading the configuration profile by sending out mass phishing emails containing a link.
"The configuration profile is an extremely sensitive iOS file which allows [them] to re-define system functionality parameters such as device, mobile carrier and network settings. The root CA [certificate authority] is what enables the threat actor to create spoofed certificates of legitimate services," said Avi Bashan. "It is important to note that the configuration profile is very simple to install. More so, many legitimate enterprise policies demand its installation."
ATTACK VECTORS
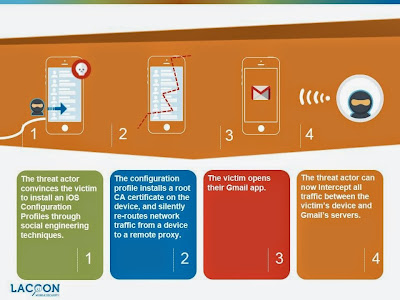
Bashan explained four simple steps that are required to perform MitM attack by exploiting the vulnerability. These are as follows:
- Hacker tricks victim into installing a configuration profile containing the root certificate and the details of the server to reroute the traffic to. (Note: to do this, a threat actor can use a variety of social engineering methods such as sending an email, purportedly from the IT department, requesting to install the configuration profile.)
- Reroutes victim’s traffic through the server under the threat actor’s control, defined by the malicious configuration profile.
- Creates spoofed certificates which are identified as valid by the victim’s device.
- Intercepts all traffic between the attacked device and intended server.
USERS OF ANDROID AND OTHER OS ARE ON THE SAFER SIDE
The certificate pinning flaw does not affect the Gmail applications running on Google’s Android or any other operating system. The vulnerability also does not affect those Gmail users who access their email on iOS through Apple’s Mail application.
Until the flaw addressed, iOS users are being advised to take precautions.
Reference- http://thehackernews.com/

No comments:
Post a Comment