At the beginning of the month, we have reported about the new surge of a Stuxnet-like malware “Havex”, which was previously targeting organizations in the energy sector, had been used to carry out industrial espionage against a number of companies in Europe and compromised over 1,000 European and North American energy firms.
Recently, researchers at security firm FireEye have discovered a new variant of Havex remote access Trojan that has capability to actively scan OPC (Object linking and embedding for Process Control)servers, used for controlling SCADA (Supervisory Control and Data Acquisition) systems in critical infrastructure, energy, and manufacturing sectors.
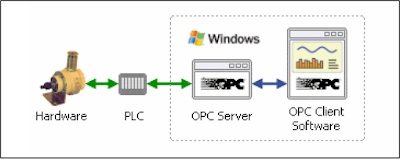
OPC is a communications standard that allows interaction between Windows-based SCADA or other industrial control systems (ICS) applications and process control hardware. New Havex variant gathers system information and data stored on a compromised client or server using the OPC standard. OPC is pervasive and is one of the most common ICS protocols.
“Threat actors have leveraged Havex in attacks across the energy sector for over a year, but the full extent of industries and ICS systems affected by Havex is unknown,” wrote the researchers from FireEye in a blog post. “We decided to examine the OPC scanning component of Havex more closely, to better understand what happens when it’s executed and the possible implications.”
Researchers set up a typical OPC server environment to conduct a real time test of the new variant's functionality. ICS or SCADA systems consist of OPC client software that interacts directly with an OPC server, which works in tandem with the PLC (Programmable Logic Controller) to control industrial hardware.
Once after getting into network, the Havex downloader calls the runDll export function and then starts scanning of OPC servers in the SCADA network.
To identify potential OPC server, the OPC Scanner module use the Windows networking (WNet) functions i.e. WNetOpenEnum and WNetEnumResources, that enumerates network resources or existing connections.
“The scanner builds a list of all servers that are globally accessible through Windows networking,” researchers wrote. “The list of servers is then checked to determine if any of them host an interface to the Component Object Models (COM).”
Using OPC scan, the new Havex variant could gather any details about connected devices and sends them back to the command-and-control server for the attackers to analyze. It appears that this new variant is used as a tool for future intelligence gathering.
“This is the first “in the wild” sample using OPC scanning. It is possible that these attackers could have used this malware as a testing ground for future utilization, however,” researchers wrote.
So far, researchers have not seen any attempt to control the connected hardware. The attack path, the developer and the intention behind the development of the malware is still not known, but researchers are investigating and trying to gather all the information about the new variant.
Reference- http://thehackernews.com/

No comments:
Post a Comment