But, if you are using the mobile version of most popular password manager from Password management company RoboForm to manage your passwords then you might be at a risk, claimed a UK based Security researcher.
I am personally using RoboForm from last few months, which is a great password manager application developed by Siber Systems Inc. for various platforms that stores your sensitive data all in one place, protected at RoboForm account and encrypted by a secret master password. RoboForm user be able to then quickly access those passwords and notes anytime, anywhere.
But a IT security consultant and tech enthusiast Paul Moore discovered one critical vulnerability in its app and one Privacy loophole in the RoboForm's service, that could allow attackers and prying eyes to get users’ personal data, including stored login credentials of various websites and payment card details.
Note: Yesterday we published this article with a conclusion that RoboForm is secure, but later after re-evaluating and discussing all factors, attack vectors with Moore, we found that RoboForm may leak your private data to attackers.
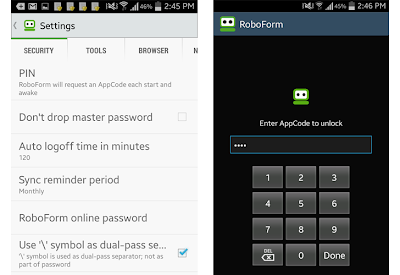
1) BYPASSING ROBOFORM DEVICE PIN PROTECTION
The vulnerability disclosed by Paul Moore in the security of RoboForm affects its Android and iOS app users, which could allow anyone to bypass RoboForm’s PIN Protection in order to access users’ sensitive data.
RoboForm mobile apps offer a PIN protection which only protects the app interface from unauthorized access, just like Android’s popular ‘AppLock’ application.
Moore claimed that simply by deleting a specific line (pref_pincode) in the RoboForm’s preferences file placed in a folder on the device file system, It was possible for Moore to access confidential data and bypass authentication process on an Android device, even without the requirement of the Master Password, as shown in the Video demonstration uploaded by him.
The important point to be noted here is that the RoboForm’s app folder which Moore claims to access is actually placed in root directory of the device, which can’t be accessed by the user or any 3rd party app on a non-rooted device.
However, RoboForm team failed to reproduce the flaw and refused the bug report. “We are not able to replicate it. As I mentioned in the write-up, it's done using an emulator, not a real device. While it's feasibly possible, it's very unlikely that the average person finding a phone with RoboForm installed could execute the precise steps needed to do what Mr. Moore is doing with the emulator.” RoboForm team said.
Yesterday, when I also failed to reproduce it myself on my Android device, then Moore explained me that even after modification, the Roboform app loads the preference file from its cache. So either Roboform app or device requires to restart in order to bypass the PIN protection.
Finally, I tried again. After restarting my Samsung Galaxy S4, I found that Roboform app opened without asking any PIN. Cool! Moore’s vulnerability works.
The vulnerability is serious, because the Roboform app stores all my passwords, secret notes and payment card details in it, and PIN bypass cloud allow anyone in 5 minutes with my phone to steal all my sensitive data.
“Additionally, our position is that if someone is able to root a phone, it's not just RoboForm that is vulnerable. Any other sensitive app would be vulnerable.” RoboForm team added.
For successful exploitation, the targeted device should be rooted or jailbroken, but it can be easily done by attackers on the stolen devices.
2.) PRIVACY LOOPHOLE: MASTER PASSWORD SECRECY
Moore believes that the company as a privacy loophole, allows them to store users’ secret master password on their server at Siber Systems. But before proceeding to the details of this loophole, you should first learn - How Roboform works.
After installing the Roboform app on Android or Windows system, it will ask you to either register or login with a RoboForm account. Once logged-in, you will get options to create or edit the payment card details, Notes and account passwords, etc.
The Mobile app or desktop software will then prompt the user to set a “Master Password” in order to encrypt the data with a strong military grade encryption. Company claims that the Master Password works like a private crypto key, used to encrypts files locally on the device and then app upload them to their server in .RFN format.
Moore claims that company stores the Master password, and asked on Twitter, "How do you decrypt online before returning the data if you don't get the key?", In Reply RoboForm said, "Paul, we decrypt the data locally, not on the servers."
Once done, the master password will get stored only on the device to automate the future encryptions and decryptions for the users’ convenience.
ROBOFORM WEB APP CAN STORE YOUR MASTER PASSWORD
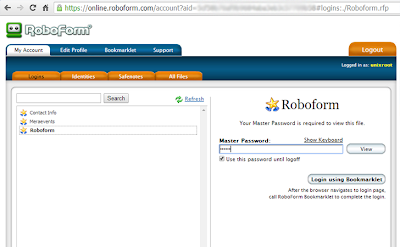
Until here, Moore and me agree that the company is not capturing our private master password on the device apps or windows apps, but Roboform Everywhere also has online web app athttps://online.roboform.com/login?lang=en location.
Using this web app hosted on Siber System servers, users can login to their Roboform account and access the stored data from the web browser, as shown:
But before accessing the encrypted data, users are required to enter their master password in order to decrypt it, that means users are sending their master keys to Siber System servers and company is decrypting the data on their servers.
The above mechanism is completely opposite and conflicts with the company's policies, which claims that they do not store users’ master key on their servers, instead they decrypt the data locally on the users’ device.
“The Server has the necessary key required to decrypt the data. Breaking the key into segments does nothing to increase security. Ultimately, it doesn't change the fact that at some point, the private key is no longer private.” Moore justified his claim.
At this moment neither I, nor Moore can proof that the company is saving your master key permanently after you once decrypt your data online via Roboform’s web app, but in this age of mass surveillance, where every company is gathering our information and damaging our privacy, it is hardly to trust on any company, like - “we get it, but we don't store it.”
CONCLUSION
PIN bypass vulnerability is working on all rooted and jailbroken devices, and it poses high risk where an app is developed with an aim to store your sensitive data securely with military grade encryption.
We can’t judge the intentions of the company, but the reported privacy loopholes could also allow government and law enforcement agencies to scrape our sensitive data by hook or crook.
The company has promised to re-evaluate the way they store the Master Password on mobile devices and will enforce the user to enter their Master Password after a reboot, even if the user chooses the option to set the Master Password to 'Off'.
“This way, if a phone is lost and a third party tries to access RoboForm either by guessing the PIN or bypassing the PIN function, the third party would still be required to know the Master Password,” said RoboForm.
Reference- http://thehackernews.com/

No comments:
Post a Comment