The critical vulnerability was identified and reported to Google Inc. late last year by researchers from German security firm Curesec. The researchers believe the virus was first noticed in Android version 4.1, also known as “Jelly Bean.”
APPS CAN MAKE CALLS FROM YOUR PHONE
“This bug can be abused by a malicious application. Take a simple game which is coming with this code. The game won’t ask you for extra permissions to do a phone call to a toll number – but it is able to do it,” Curesec’s CEO Marco Lux and researcher Pedro Umbelino said Friday in a blog post. “This is normally not possible without giving the app this special permission.”
By leveraging these vulnerabilities, malicious applications could initiate unauthorized phone calls, disrupt ongoing calls, dialing out to expensive toll services, potentially framing up big charges on unsuspecting users' phone bills.
Android bug allows unauthorized users to terminate outgoing calls and Send USSD
The vulnerability can also be exploited to disconnect the outgoing calls, to send and execute :
- Unstructured Supplementary Service Data (USSD)
- Supplementary Service (SS)
- Manufacturer-defined MMI (Man-Machine Interface) codes.
These special codes can be used to access various device functions or operator services, which makes the problem a nasty one for those who value the data they store on their mobile phone.
“The list of USSD/SS/MMI codes is long and there are several quite powerful ones like changing the flow of phone calls (forwarding), blocking your SIM card, enabling or disabling caller anonymisation and so on,” reads the blog post.
Even the Android security programs, where apps without the CALL_PHONE permission should not be able to initiate phone calls, can be easily bypassed and offer no protection from these flaws, because the exploits have capability to deceive the Android permissions system altogether.
"As the app does not have the permission but is abusing a bug, such apps cannot easily protect you from this without the knowledge that this bug exists in another class on the system," wrote the researchers.
A large number of versions of Android are affected by the vulnerabilities. Researchers have found two different flaws that can be exploited to achieve the same ends – one that's present in newer Android releases and another that's found in older versions.
FIRST BUG - AFFECTS NEWER VERSION OF ANDROID
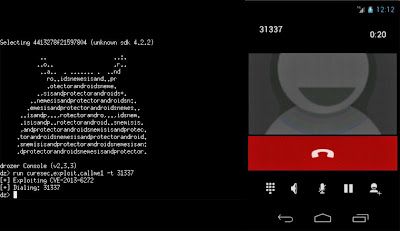
The first security bug, identified as CVE-2013-6272, appears to be introduced in Android version 4.1.1 Jelly Bean, and outlasted all the way through 4.4.2 KitKat before the security team at Google was able to fixed it in Android 4.4.4.
But, luckily only about 14% of users are currently updated to the latest version of the mobile Operating System. So, just think about it, How many users are currently in the grip of the flaws? Not less than a generous users open to vulnerabilities and attack paths.
SECOND BUG - AFFECTS OLDER VERSION OF ANDROID
The second security hole is wider in its reach, affecting both Android 2.3.3 and 2.3.6, the popular versions of Gingerbread variant which are used by lower-end smartphones, budget-style smartphones which continue to surge in popularity amongst emerging markets like those found in Brazil, China, and Russia.
The bug was fixed in Android 3.0 Honeycomb, but that was a tablet-only release that no longer even charts on Google's Android statistics. That means the bugs leave nearly 90 percent of Android users running vulnerable versions of the Operating System to dialer-manipulating vulnerability.
Researchers at Curesec have provided source code and a proof-of-concept demonstration app for both the bugs, so that customers can help themselves to test if their Android devices are vulnerable or not.
It is strongly advised to Android users those are running KitKat on their devices to get upgraded to the latest version 4.4.4 as soon as possible. It is expected that the device makers and carriers will soon roll out the updates in the coming weeks.
Reference- http://thehackernews.com/
No comments:
Post a Comment