“Inside Microsoft’s Insider Program you'll get all the latest Windows preview builds as
Sunday 5 October 2014
Windows 10 Preview Has A Keylogger to Watch Your Every Move
Tuesday 23 September 2014
The Pirate Bay Runs on 21 "Raid-Proof" Virtual Machines To Avoids Detection
The Pirate Bay is the world's largest torrent tracker site which handles requests from millions of users everyday and is in the top 100 most visited websites on the Internet. Generally, The Pirate Bay is famous for potentially hosting illegal contents on its website.
Despite years of persecution, it continues to disobey copyright laws worldwide. Even both the founders of The Pirate Bay (TPB) file exchange service were arrested by the
'Facebook To Begin Charging Users $2.99 / Month' — Totally BULLSHIT!
Facebook going to charge users per month?? Nobody expected such a news story this week, but it seems that Facebook will No longer be a Free Service, according to reports claimed by the National Report, "Facebook To Begin Charging Users $2.99/mo Starting November 1st", which turns out fake. Thank God !!
This new report is circulating via social media which claims that the social networking giant
Monday 22 September 2014
How To Run Almost Any Android App On Windows, OS X, Linux with Chrome
Malicious Google DoubleClick Advertisements Distributed Malware to Millions of Computers
A recent report published by the researcher of the security vendor Malwarebytes suggests
Wednesday 10 September 2014
Unmasking Google Users With a New Timing Attack
Andrew Cantino, the vice president of engineering at Mavenlink, detailed his attack in a blogpost st week. According to him, the attack could be used by an attacker to target a particular person or organization. A cyber criminal could share a Google document with an
Israeli Think Tank Compromised to Serve Sweet Orange Exploit Kit
The Israeli think tank website JCPA – an independent research institute focusing on Israeli security, regional diplomacy and international law – was serving the Sweet Orange exploit
Monday 8 September 2014
Chinese Government Accused of Intercepting Traffic Between Google and CERNET
So far, we all are well aware of the fact that Chinese have had a past filled with cases of Cyber Crime. China is the world’s largest exporter of IT goods, but it has been criticized by many countries due to suspected backdoors in its products, including United States which has banned its several major government departments, including NASA, Justice and Commerce Departments, from purchasing Chinese products and computer technology. The new exposure indicates the same.
Chinese Government is running a man-in-the-middle (MitM) cyber attack campaign on SSL encrypted traffic between the country’s education network and Google.
In an effort to monitor its users of China Education and Research Network (CERNET), Chinese authorities has started intercepting encrypted traffic to and from Google’s servers, the non-profit organization GreatFire reported on Thursday.
However, just like many other foreign websites, Google is blocked in China. Because Google is one of the vast and valuable website for research purpose, Chinese authorities allow access to it through CERNET, a nationwide education and research computer network.
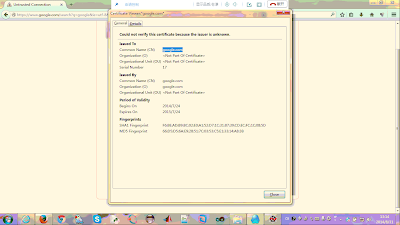
The story broke when CERNET users started reporting on social media websites that they are receiving warning messages about invalid SSL certificates when they try to access google.com and google.com.hk through CERNET.
According to the non profit organisation GreatFire, the Chinese authorities have launched a man-in-the-middle (MitM) attack against the encrypted traffic between CERNET and Google in an effort to control the media as well as messages on all fronts.
The present authorities feel that blocking Google might receive an angry rebuttal from students, researchers, and educators throughout the country, so MitM attack will solve the purpose.
“Instead of just outright blocking Google on CERNET, which would have raised the ire of students, educators and researchers across China, the authorities felt that a MITM attack would serve their purpose. By placing a man-in-the-middle, the authorities can continue to provide students and researchers access to Google while eavesdropping or blocking selective search queries and results,” GreatFire reported in a blog post.
With the help of MitM attack, Chinese authorities were spying on users’ search queries and their results. GreatFire said that they concluded the result after following the expert advice from Netresec, a security-based company that analyzed the MITM attacks on Github.
Until last month, CERNET users could able to access the search engine Google freely, but after 28 August, there have been changes and users receive a certificate expiration page warnings when they search for something.
Experts believe that the devices which are performing MitM attack may be injecting packets near the outer border of CERNET, the place where it peers with external networks. However, Netresec researchers said that it’s difficult to figure out how the attack was planned, but DNS spoofing was certainly not used.
“It’s difficult to say exactly how the MITM attack was carried out, but we can dismiss DNS spoofing as the used method. A more probable method would be IP hijacking; either through a BGP prefix hijacking or some form of packet injection. However, regardless of how they did it the attacker would be able to decrypt and inspect the traffic going to Google,” Netresec researchers noted in a blog post.
This isn’t the first time Chinese government launched such attack, the authorities conducted similar attacks in the past, in January 2013, against developer site Github. Users of GitHub service in China reported receiving warning messages about invalid SSL certificates.
Reference- http://thehackernews.com/
Sunday 7 September 2014
Fake Flappy Bird App Planted by Hackers to Steal Photos from Device
As far, you have probably heard about the biggest digital exposure of private and very personal nude photographs of as many as 100 female celebrities including Jenny McCarthy, Kristin Dunst, Mary E Winstead, and Oscar winner Lawrence and Kate Upton, that was surfaced on notorious bulletin-board 4chan, and anonymous image board AnonIB over the weekend.
It was believed that the group of hackers allegedly taken celebrities photos from
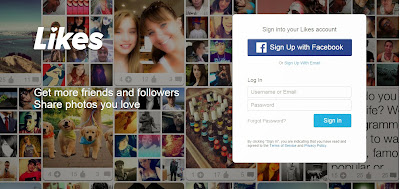
Popular Photo Sharing Website Likes.com Vulnerable To Multiple Critical Flaws
Likes.com, one of the emerging social networking site and popular image browsing platform, is found vulnerable to several critical vulnerabilities that could allow an attacker to completely delete users’ account in just one click.
Likes.com is a social networking website that helps you to connect with people you like and make new friends for free. Just like any other social place, users can always follow their favorite tag or people who catch their fancy. It is much easier to use and is designed for those who want to look at pictures different people upload.
Apple to Add Security Alerts for iCloud Users after Celebrity Nude Photo Hack
In the wake of the biggest digital exposure of personal nude selfies belonging to as many as 100 high-profile celebrities, Apple said the company plans to add extra security measures to keep hackers out of user accounts.
Not just this, the company also plans to extend its two-factor authentication (2FA) feature to account logins to the iCloud service from mobile device in order to avoid future
Malware Can Bypass Chrome Extension Security Feature Easily
Security experts at TrendMicro believe that the malware is triggered by opening Facebook or Twitter via shortened links provided in any social networking websites. Once clicked, the links may lead victims to a site that automatically downloads the malicious browser
Facebook Rolling Out Privacy Checkup for Users
The social networking giant on Thursday rolled out its "Privacy Checkup" tool that will help its more than 1.2 billion users to audit their privacy settings on Facebook to make
Friday 5 September 2014
Cyber Espionage Group Ported Windows Malware to Mac
GROUP BEHIND THE MAC VERSION OF BACKDOOR
Researchers have unmasked a group of cyber criminals that has recently started using a new variant ofXSLCmd backdoor program to target Mac OS X systems. This Mac version
Microsoft to Patch Critical Internet Explorer Vulnerability Next Week
Today Microsoft has released its Advance Notification for the month of September Patch
Thursday 4 September 2014
Fake Cell Phone Towers Could Be Intercepting Your Calls
The research carried out by ESD America, a defense and law enforcement technology firm based in Las Vegas, shows that a rogue cell phone towers, also known as "interceptors", may process the call.
ESD America, the company that makes the super-secure CryptoPhone, makes one of the oldest and most expensive high-security cell phones in the market. It provides equipment and training to more than 40 countries with a goal to provide technical security assistance to government and corporate clients across Asia.
SEVERAL ROGUE CELL PHONE TOWERS DISCOVERED
While field-testing its secure Android handset, the CryptoPhone 500, the firm came across the existence of a series of fake base stations along the Eastern seaboard of the US. Les Goldsmith, the CEO of ESD America, told the US publication Popular Science that he found 17 mobile phone towers across the U.S. that forces the phone to backdown to an easy-to-break 2G connection and then switches off the encryption.
"What we find suspicious is that a lot of these interceptors are right on top of U.S. military bases. So we begin to wonder – are some of them U.S. government interceptors? Or are some of them Chinese interceptors?" he says.
MAN-IN-THE-MIDDLE ATTACK
No one knows for sure who's running them, Goldsmith said. He called these fake phony towers as“interceptors” on the basis that they might be attempting man-in-the-middle (MitM) attacks, in cases where the rogue tower takes a phone call, siphons it off for interception and also passes it on to the legitimate network.
Here's how interceptors exploit your smartphones:
“[Interceptors] are radio-equipped computers with software that can use arcane cellular network protocols and defeat the onboard encryption. Whether your phone uses Android or iOS, it also has a second operating system that runs on a part of the phone called a baseband processor. The baseband processor functions as a communications middleman between the phone's main O.S. and the cell towers. And because chip manufacturers jealously guard details about the baseband O.S., it has been too challenging a target for garden-variety hackers.”
WHAT ABOUT SAMSUNG AND iPHONE
Goldsmith said when his team drove to a US government facility in the Nevada desert in the month of July, he also took a standard Samsung Galaxy S4 and an iPhone to serve as a control group for his CryptoPhone 5000. The CryptoPhone "lit up like a Christmas tree", while his iPhone and Samsung Galaxy S4 showed no signs of being intercepted at all.
"As we drove by, the iPhone showed no difference whatsoever. On the Samsung Galaxy S4, the call went from 4G to 3G and back to 4G. The CryptoPhone lit up like a Christmas tree," he said.
WHO IS BEHIND THESE INTERCEPTORS
In this case, the problem is that the phones never alert the user if the encryption was switched off when it managed to associate with these interceptors.
So, a question arises here, Who is responsible for these interceptors? In one particular case one of these towers was discovered at a casino in Las Vegas as well as near several military installations.
“Edward Snowden revealed that the N.S.A. is capable of an over-the-air attack that tells the phone to fake a shut-down while leaving the microphone running, turning the seemingly deactivated phone into a bug,” reported Popular Science.
“And various ethical hackers have demonstrated DIY interceptor projects, using a software programmable radio and the open-source base station software package OpenBTS – this creates a basic interceptor for less than $3,000. On August 11, the F.C.C. announced an investigation into the use of interceptors against Americans by foreign intelligence services and criminal gangs.”
SOLUTION - CRYPTOPHONE OF $3,500
So, in order to protect from these fake phony towers or interceptors, do we need a CryptoPhone?
According to Popular Science, if you're not realistically of any interest to the U.S. government and never leave the country, you probably don't. In fact, the primary customers of CryptoPhone are executives who do business in Asia, according to Goldsmith.
The important part to decide whether you need a CryptoPhone is that, a single CryptoPhone costs $3,500, five times the price of competitors like SGP Technologies' Blackphone. So even if you are looking for a one, it's not exactly an impulse buy.
Plus, as Goldsmith told the MIT Technology Review back in March, his company hasn't been able to make these boutique phones fast enough, ever since the NSA scandals erupted last year.
Reference- http://thehackernews.com/
Apple Patches 'Find My iPhone' Vulnerability Which May Caused Celebrities Photo Leak
OVER 100 CELEBRITIES AFFECTED
So far, I hope everybody have heard about probably the biggest digital exposure of personal nude photographs belonging to as many as 100 high-profile celebrities, including Jenny McCarthy, Kristin Dunst, Mary E Winstead, and the Oscar winning actress Jennifer
LinkedIn Boosts Security With New Session Alert and Privacy Control Tools
With a need to give more controls in users’ hands, LinkedIn has introduced a few new security features that the company says will help users of the social network for professionals keep their accounts and data more secure.
SESSION ALERTS
Just like Google, Facebook, Yahoo and other online services, LinkedIn has added a new option within the settings tab that allows users to see where and on what devices they are
New Firefox 32 Adds Protection Against MiTM Attack and Rogue Certificates
The new version of Firefox makes the browser even more competitive among others. Firefox version 32 has some notable security improvements, including a new HTTP cache for improved performance,public key pinning - a defense that would help protect its
Wednesday 3 September 2014
Namecheap Accounts Compromised in Data Breach
The Hosting company confirmed the security breach and informed that the hackers have compromised some of its customers’ accounts, probably using the "biggest-ever" password theft via Russian Hackers that disclosed list of 1.2 billion usernames and passwords compiled
Tuesday 2 September 2014
Reported Apple iCloud Hack Leaked Hundreds of Nude Celebrity Photos
The recent privacy breach appears to be one of the biggest celebrity privacy breaches in history and represents a serious offense and violation of privacy. A hacker allegedly breached
Monday 1 September 2014
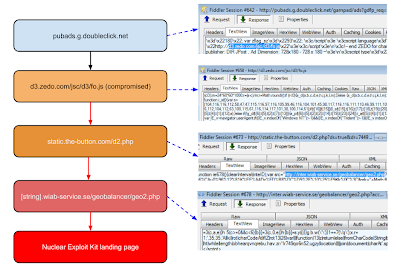
Malicious Advertisements Found on Java.com, Other High-Profile Sites
AppNexus servers process 16 billion ad buys per day, making it the biggest reach on the open web after Google. Back in May, AppNexus was serving malicious ads targeting Microsoft’s Silverlight platform. The world’s largest Internet Video Subscription service Netflix runs on Silverlight, and because of its popularity, hackers have been loading exploit kits with Silverlight.
As part of this campaign, users of several high-profile websites including Java.com, Deviantart.com, TMZ.com, Photobucket.com, IBTimes.com, eBay.ie, Kapaza.be and TVgids.nl, last week were redirected to websites serving malicious advertisements that infected visitors by installing botnet malware on their computer, said security company Fox-IT.
“These websites have not been compromised themselves, but are the victim of malvertising. This means an advertisement provider, providing its services to a small part of a website, serves malicious advertisement aimed at infecting visitors with malware,” researchers at Fox-IT said in a blog post.
Angler exploit kits are available on the underground black forums and are used in various malicious campaigns to own websites and redirect users off to websites hosting banking malware and other types of malicious code in order to victimize them.
“Please note, a visitor does not need to click on the malicious advertisements in order to get infected. This all happens silently in the background as the ad is loaded by the user’s browser,” researchers warned.
According to the Researchers, Angler first checks whether the victim’s browser supports an outdated versions of Java, Adobe Flash Player or Microsoft Silverlight, and then silently install a variant of the Asprox botnet malware.
Asprox is generally a spam botnet that was involved in multiple high-profile attacks on various websites in order to spread malware. The malware recently has been modified for click-fraud and cyber criminals are using it to spread malware through email attachments with exploit kits. It also has other malicious functionality including scanning websites for vulnerabilities and stealing log-in credentials stored on computers.
“Asprox has gone through many changes and modifications which includes spam modules, website scanning modules and even credential stealing modules,” Fox-IT said. “This history and current events show Asprox is still actively being developed and used.”
Once visited on a site hosting the malicious ad, users are redirected in the background to ads[.]femmotion[.]com, which then redirects to the exploit kit on a number of other domains, the gloriousdead[.]com and taggingapp[.]com.
“All the exploit kit hosts were observed using port 37702. Running exploit kits on high ports at best prevents certain network tools from logging the HTTP connections, as these are typically configured to monitor only HTTP ports,” Fox-IT said. “It does mean this exploit kit is blocked on a lot of corporate networks as they do not allow for browsing outside the normal HTTP ports, port 80 (or proxy ports) and 443 for SSL.”
In order to show targeted advertisements to users, advertisers engage in an automatic, real-time bidding process, which makes malicious advertisements more difficult to track. “In the case of this malvertising campaign the malicious advertisers were the highest bidders,” Fox-IT says.
Hackers used a method called “retargeting”, which is actually used by Digital Advertising agencies to rotate the ads shown to the same visitor when they access a specific page multiple times.
“The way it works is that a user with an interesting set of tracking cookies and other metadata for a certain adprovider is retargetted from the original advertisement content on the website to the modified or personalized data,” Fox-IT researchers said. “We have seen examples where the website that helped with the ad redirect to infect a user had no idea it was helping the delivery of certain content for a certain ad provider.”
Reference- http://thehackernews.com/
Thursday 28 August 2014
Google Chrome 64-bit Browser Finally Released As a Stable Version
Back in June, Google first released Chrome 64-bit only in the browser’s Dev and Canary
Monday 25 August 2014
Sony PlayStation Network Taken Down By DDoS Attack
It's possible that EVE Online and Guild Wars 2 have also been hit by the attackers. Developers on the EVE Online forums have announced DDoS issues, and many users on the Guild Wars
Sunday 24 August 2014
Hacking Gmail App with 92 Percent Success Rate
Computer scientists the University of California Riverside Bourns College of Engineering and the University of Michigan have identified a new weakness they believe to exist in Android,
Facebook Awards $50,000 Under Its New 'Internet Defense Prize' Program
Till now, a number of large technology companies have bug bounty programs to reward researchers and cyber enthusiast who contribute in the security of Internet by finding out security holes in software or web platforms, and the social networking giant Facebook is the
Remote Attack Could Format Your Pebble Smartwatch Easily
Pebble Smartwatch, developed and released by Pebble Technology Corporation in 2013, is considered as one of the most popular SmartWatches that had become the most funded project in the history of Kickstarter. Just two hours after its crowd-funding campaign
Thursday 21 August 2014
Hacking Traffic Lights is Amazingly Really Easy
The hacking scenes in hollywood movies has just been a source of entertainment for the technology industry, like we've seen traffic lights hacked in Die Hard and The Italian Job, but these movies always inspire hackers to perform similar hacking attacks in day-to-day life.
AlienVault Releases Intrusion Detection Systems (IDS) Best Practices
Monday 18 August 2014
Hillary Clinton's Phone Intercepted by German intelligence Agency
After the allegations that the U.S. National Security Agency (NSA) not only conducted mass surveillance on German citizens, but also spied on German Chancellor Angela Merkel’s own personal mobile phone for years, surveillance has become a big issue for Germany. So big, that Germany itself started spying on U.S.
According to the reports came from the German media on Friday, the German foreign
Subscribe to:
Posts (Atom)