Geodo, a new version of the infamous Cridex (also known as Feodo or Bugat) banking information stealing Trojan works in conjunction with a worm that sends out emails automatically to continue its self-spreading infection method, effectively turning each infected Windows system in the botnet for infecting new targets, Seculert warned.
The Infected Windows systems in the botnet network download and install an additional piece of malware (i.e. an email worm) from the Botnet's command and control servers, provided with approximately 50,000 stolen SMTP account credentials including those of the associated SMTP servers.
The stolen SMTP credentials appeared to come from Cridex victims and with the help of those credentials, the malware then sends out emails from legitimate accounts to other potential victims, masquerading itself as a bank or financial organization, in an effort to continue its spread and majority of targets (over 46%) mostly belongs to Germany.
“The C&C provides the malware with a batch of 20 targeted email addresses.The malware is also given a from address, subject line, and email body text unique to this particular batch of emails. Once the malware has run through the batch, it is provided with a new batch of 20 emails. And with each new batch of emails the C&C also sends a new from address, subject line, and body.”
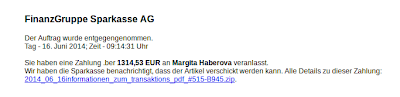
"The emails we have seen, written in German, contain a link prompting the recipient to download a zip file which contains an executable disguised as a PDF document," Seculert explains in a blog post published yesterday. "By opening the file, Geodo [new version of Cridex] is installed on the newly infected endpoint, adding a new bot to the mix.”
Cridex is a banking worm that targets banks from around the world. It was traditionally been distributed via removable drives, or a malicious file dropped by other malware or unknowingly download of a file by users when visiting malicious sites.
After infection, when the user connects to his banking website, the variant malware selects the malicious code designed specifically for that bank and injects it into the user’s browser. Ultimately, the injected script will attempt a money transfer.
Previous variants of Geodo are still targeting victims primarily from Germany, Austria, Hungary and the United States using phishing attack. Phishing mails include a link to download a zip file containing the malware disguised as an invoice or Shipment PDF file.
Previous variants of Geodo are still targeting victims primarily from Germany, Austria, Hungary and the United States using phishing attack. Phishing mails include a link to download a zip file containing the malware disguised as an invoice or Shipment PDF file.
Malware that steals banking credentials has been a known problem for years, but now the threat is delivered directly to users from the email addresses of other innocent users, which has capability to spread by itself and compromises the intellectual property of a corporation, putting its business and reputation at risk.
Reference- http://thehackernews.com/

No comments:
Post a Comment