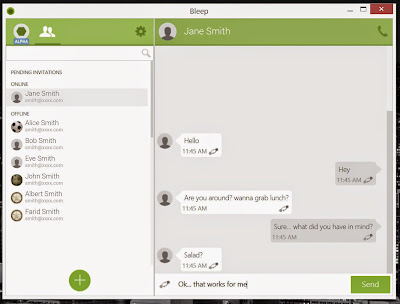
BitTorrent named its Online chat service as "Bleep", a decentralised peer-to-peer voice and text communications platform that offers end-to-end encryption, therefore is completely safe
Thursday 31 July 2014
BitTorrent Unveiled New Decentralized "Bleep" Instant Messenger
Facebook's Internet.Org App Offers Free Internet in Zambia
Dream comes true! Facebook Inc. (FB) in partnership with Bharti Airtel Ltd. (BHARTI) of
Russian Government Asks Apple to Hand Over iOS and Mac Source Code
APPLE & SAP, HAND OVER YOUR SOURCE CODES
Russian government has asked Apple to provide the access to the company’s source code in
Wednesday 30 July 2014
Attackers Compromise TOR Network to De-Anonymize Users of Hidden Services
A critical vulnerability in Tor — an encrypted anonymizing network considered to be one of the most privacy oriented service, which is used by online users in order to hide their activities from law enforcement, government censors and others — was probably being used to de-anonymize the identity of Tor users, Tor project warned on Wednesday.
115 MALICIOUS ToR RELAYS WERE DE-ANONYMIZING USERS
According to a security advisory, Tor Team has found a group of 115 malicious fast non-
Instasheep — Instagram Account Hacking Tool Released
Two days ago, we reported at The Hacker News about a critical issue in the most popular image and video sharing service, Instagram app for mobiles, that allows an attacker to hijack users’ account and successfully access private photos, delete victim's photos, edit comments and also post new images.
Yesterday, a London developer Stevie Graham has released a tool called “Instasheep” a play
Signal — Open Source iPhone App to Make Free End-to-End Encrypted Voice Calls
When we talk about the privacy of our messages and voice calls, Open Whisper Systems has
Android "Fake ID" Vulnerability Allows Malware to Impersonate Trusted Apps
Researchers at BlueBox security, who identified the vulnerability, dubbed the flaw as Fake ID, which affects all versions of Android operating system from 2.1 (released in 2010) up to
Tuesday 29 July 2014
Facebook Self-XSS Scam Fools Users into Hacking Themselves
Not by serving fake post, neither by providing malicious video link, instead this time scammers have used a new way of tricking Facebook users into injecting or placing
Chinese Hackers Stole Blueprints of Israel's Iron Dome Missile Defense System
Chinese hackers infiltrated the databases of three Israeli defense contractors and stole plans for Israel's Iron Dome missile defense system, according to an investigation by a Maryland-based cyber security firm ‘Cyber Engineering Services Inc. (CyberESI)’.
Not just this, the hackers were also able to nab plans regarding other missile interceptors, including Unmanned Aerial Vehicles, ballistic rockets and the Arrow III missile interceptor
Instagram Mobile App Issue Leads to Account Hijacking Vulnerability
In the era of Government surveillance, ensuring the security and safety of our private communications regardless of platform – email, VOIP, message, even cookies stored – should be the top priority of the Internet industry. Some industry came together to offer Encryption as the protection against government surveillance, but some left security holes that may expose your personal data.
A critical issue on Instagram’s Android Application has been disclosed by a security
Researcher to Demonstrate Poor SSL Implementations Using Pineapple WiFi
There are thousands of websites over Internet that contain serious mistakes in the way that
Sunday 27 July 2014
Kali Linux 1.0.8 — New Release Supports UEFI Boot
Kali Linux is based upon Debian Linux distribution designed for digital forensics and penetration testing, including a variety of security/hacking tools. It is developed, maintained
Russian Government Offers $111,000 For Cracking Tor Anonymity Network
The Russian government is offering almost 4 million ruble which is approximately equal to $111,000 to the one who can devise a reliable technology to decrypt data sent over the Tor, an encrypted anonymizing network used by online users in order to hide their activities from law enforcement, government censors, and others.
The Russian Ministry of Internal Affairs (MVD) issued a notice on its official procurement
Intel launches Hardware-based Self-Encrypting Solid State Drives
Once a bad actor has stolen your hardware or compromised your network, the ability to lock
Mayhem — A New Malware Targets Linux and FreeBSD Web Servers
Researchers dubbed the malware as Mayhem, a nasty malware modular that includes a number of payloads to cause malicious things and targets to infect only those machines
Thursday 24 July 2014
Exploit-Selling Firm Kept Internet Explorer Zero-Day Vulnerability Hidden for 3 Years
A French information security company VUPEN has recently disclosed that it held onto a serious Internet Explorer (IE) vulnerability for at least three years before revealing it at the Pwn2Own hacker competition held in March this year.
The critical zero-day vulnerability affected versions 8, 9, 10 and 11 of Internet Explorer
50,000 Websites Hacked Through MailPoet WordPress Plugin Vulnerability
The users of WordPress, a free and open source blogging tool as well as content management system (CMS), that have a popular unpatched wordPress plugin installed are being cautioned to upgrade their sites immediately.
A serious vulnerability in the WordPress plugin, MailPoet, could essentially allows an
HTML5 Canvas Fingerprint — Widely Used Unstoppable Web Tracking Technology
This summary is not available. Please
click here to view the post.
Warning — Zero-Day Vulnerabilities Identified in Tails Operating System
The critical zero-day security flaws has been discovered in the privacy and security dedicated Linux-based operating system “Tails” that could be used by an attacker to unmask your identity.
Tails, which is been used and recommended by the global surveillance whistleblower Edward Snowden to remain Anonymous, has a suite of privacy applications and designed to keep
Apple Strongly Denies Claims of Installing iOS Backdoor
The allegations from a data forensic expert and security researcher that iOS contains a “backdoor”permitting third parties to potentially gain access to large amount of users' personal data instigated Apple to give a strong response.
The company has completely denied to the claims published over the weekend by Jonathan Zdziarski, a forensic scientist and iOS security expert.
Firefox 31 — Mozilla Releases Security Updates to Tighten Browser Security
Mozilla has officially released its latest build Firefox 31 for all supported platforms, addressing 11 vulnerabilities in total, three of which are marked critical that could have been exploited by hackers to mount remote code execution attacks.
Mozilla Firefox recommends its users to install the security update as soon as possible, warning that the three critical vulnerabilities discovered in its browser could be exploited by attackers and leverage them to "run attacker code and install software, requiring no user
Tuesday 22 July 2014
Indexeus — Search Engine Exposes Malicious Hackers and Data Breaches
Now, a new search engine has been launched that primarily exposes all the available information of malicious hackers caught up in the very sort of data breaches — including the recent massive breaches at Adobe and Yahoo!
The search engine dubbed as “Indexeus”, designed by 23-year-old Jason Relinquo of Portugal, boasts a searchable database of "over 200 million entries available to our customers". It specifically targeted hackers by listing huge amounts of their information such as email addresses, usernames, passwords, Internet address, physical addresses, birthdays and other information that may be associated with those accounts.
If in case, any hacker want to get their credentials removed or blacklisted from the search engine, it would cost $1per record that they wanted to conceal from public view.
As a disclaimer on the search engine website explained, "The purpose of Indexeus is not to provide private informations about someone [sic], but to protect them by creating awareness. Therefore we are not responsible for any misuse or malicious use of our content and service."
Most of the information this 23 year old boy gathered comes from data breaches and hacks of forums popular in the hacking community, which no doubt makes it one of the largest depositories of hackers' personal details ever made available publicly.
The search engine website says that its purpose is to make people more aware of their online security, which they sometimes undermine.
“This is a service which provides easy access to hundreds of databases, which is very useful if you don't want to bring your databases around or if you just don't have any,” reads the website’s FAQ page. “The goal is to make people realize that using the same information all over is stupid and will lead to you getting your information stolen, but also showing you how badly administrators keep your private data stored.”
Apparently, you no longer have to pay for the removal of any record -- it’s free now. Since being exposed by Brian Krebs, Relinquo recently modified his terms of service so that users don't have to pay any dollar to have their information removed or completely blacklisted from the search engine’s site.
Obviously, due to the EU's "right to be forgotten;" he can not charge for a service that's supposed to be free of charge. However, it remains unclear how users would prove that they are the rightful owner of specific records indexed by the service.
"We're going through some reforms (free blacklisting, plus subscription based searches), due some legal complications that I don't want to escalate," Relinquo wrote in a chat session. "If [Indexeus users] want to keep the logs and pay for the blacklist, it's an option. We also state that in case of a minor, the removal is immediate.”
If the availability of private information made Relinquo able to build the search engine, then you can imagine what amount of private informations of users breached in different hack attacks. It indicates that online privacy and security threats are real, since hackers may already have a user’s information without even their knowledge.
However for now, Relinquo have made the removal of information for free, but if it is assumed that $1 per record had actually happened, it would have made him million dollars.
Reference- http://thehackernews.com/
'Real Footage of Malaysian Flight MH 17 Shot Down' Facebook Spam Spreads Malware
A distasteful trend among the cyber crooks have began these days that they left no occasion, either good or bad, to snatch users’ financial information in order to make money as well as spread malware to victimize users.
The tragedy of the crashed Malaysia Airlines flight MH17 is no exception for the criminal minds. They are exploiting the disaster that took place last week in the disputed territory.
Undocumented iOS Features left Hidden Backdoors Open in 600 Million Apple Devices
A well known iPhone hacker and forensic scientist has unearthed a range of undocumented and hidden functions in Apple iOS mobile operating system that make it possible for a hacker to completely bypass the backup encryption on iOS devices and can steal large amounts of users’ personal data without entering passwords or personal identification
Monday 21 July 2014
Critroni - File Encrypting Ransomware out in the Wild
The latest ransomware, given the name “Critroni”, includes a number of odd features that makes it out of the ordinary and according to the researchers, it’s the first ever Crypto ransomware seen that uses the Tor anonymizing network for command and control to conceal its communication.
According to a detailed analysis of the ransomware threat by a French security researcher
Cydia Repository by BigBoss Hacked, All Paid and Free Tweaks Stolen
BigBoss repository, one of the biggest and most popular repositories for jailbreak tweaks in Cydia, has reportedly been hacked by either an individual or a group of hackers.
Cydia is a software application for iOS that enables a user to find and install software packages on jailbroken iOS Apple devices such as the iPhone, the iPod Touch, and the iPad. Most of the software packages available through Cydia are free, but some require
How Russian Hackers Placed "Digital Bomb" Into the NASDAQ
Four years ago, NASDAQ servers were compromised by Russian hackers, who were somehow able to insert a "digital bomb" into the systems of NASDAQ stock exchange, which would have been able to cause several damage to the computer systems in the stock market and could bring down the entire structure of the financial system of the United States.
Till now, identities of the hackers have not been identified by the agencies who are
Sunday 20 July 2014
Cyber Criminals Use Malaysia Airlines Flight MH17 Plane Crash News to Bait Users
According to the U.S. intelligence officials, Malaysia Airline Flight MH17, a Boeing 777 aircraft
New Variant of Havex Malware Scans for OPC Servers at SCADA Systems
At the beginning of the month, we have reported about the new surge of a Stuxnet-like malware “Havex”, which was previously targeting organizations in the energy sector, had been used to carry out industrial espionage against a number of companies in Europe and compromised over 1,000 European and North American energy firms.
Recently, researchers at security firm FireEye have discovered a new variant of Havex remote
Friday 18 July 2014
NSA Employees Routinely Pass Around Intercepted Nude Photos
The 31-year-old former US National Security Agency (NSA) contractor Edward Snowden has warned that during surveillance, among other things, NSA system administrators also intercepted and routinely passed the nude photos of people in "sexually compromising" situations among other NSA employees.
In a video interview, NSA whistleblower speaks with the Guardian editor-in-chief Alan
Thursday 17 July 2014
New Pushdo Malware Hacks 11,000 Computers in Just 24 Hours
Pushdo, a multipurpose Trojan, is primarily known for delivering financial malware such as ZeuS and SpyEye onto infected computers or to deliver spam campaigns through a commonly associated components called Cutwail that are frequently installed on
FBI — Botnets Infecting 18 Computers per Second. But How Many of Them NSA Holds?
Botnets - a secretly compromised networks of ordinary home and office computers with rogue software or "malware" that are controlled by an individual criminal or a group - has dramatically increased over the past several years and are considered to pose the biggest threat to the Internet.
Cyber criminals have brushed-up their hacking skills and are using Botnets as a cyber
Multiple Cisco Wireless Gateways Vulnerable to Remote Attacks
Cisco announced that a number of its Wireless Residential Gateway products are vulnerable to a remote-code execution attack, which is exploited by sending a specially crafted HTTP
Wednesday 16 July 2014
Germany to Consider Typewriters to Protect From US Spying
So far we have heard that using privacy tools by every individual and offering encrypted communication by every company is the only solution to Mass Surveillance conducted by the government and law enforcement authorities. But, Germany says the only solution to guard against surveillance is - Stop using Computers!!
Ohh Please!! Is it a joke?
No, it does not mean that they are going to completely throw out all of their computer
Update Your Java to Patch 20 Vulnerabilities Or Just Disable it
Today, Oracle has released its quarterly Critical Patch Update (CPU) for the month of July, as part of its monthly security bulletin, in which it fixes a total of 113 new security vulnerabilities for hundreds of the company’s products.
The security update for Oracle’s popular browser plug-in Java addresses 20 vulnerabilities in the software, all of which are remotely exploitable without authentication, that means an
Subscribe to:
Posts (Atom)