Cross-Site Request Forgery is a method of attacking a Web site in which an intruder masquerades as a legitimate and trusted user. All the attacker need to do is get the target browser to make a request to your website on their behalf. If they can either:
- Convince your users to click on a HTML page they've constructed
- Insert arbitrary HTML in a target website that your users visit
Not too difficult, is it?
Abdullah Hussam, a 17 years old programmer from Iraq found that just by modifying parameters value of a Flickr HTTP request, one can trick the web service to modify users’ profiles.
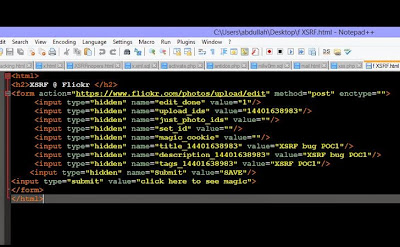
When a user uploads a photo on Flickr, it will redirect the user to the page where they can add info on the photo like tags, description, and title. The request it make is as shown below:
edit_done=1&upload_ids=14401638983&just_photo_ids=&set_id=&magic_cookie=32e285e98bbef3aa6afd8c879891c01b&title_14401638983=XSRF+bug+POC1&description_14401638983=XSRF+bug+POC1&tags_14401638983=XSRF+POC1&tags_14401638983=XSRF+POC2&Submit=SAVE
According to Abdullah, the flaw resides in the "magic_cookie" parameter, which Flickr used to protect its website users from XSRF vulnerability.
In order to exploit Flickr XSRF vulnerability, an attacker can simply setup a webpage on his server with custom HTML form and custom parameter values, as shown. By keeping "magic_cookie" parameter value empty and changing Photo ID to the new image ID, the exploit will be able to bypass protection mechanism.
When the victim clicks a button on the web page, it generates a manipulated HTTP request to the server, which force the Flickr to replace victim's profile image with new image.
When the victim clicks a button on the web page, it generates a manipulated HTTP request to the server, which force the Flickr to replace victim's profile image with new image.
“The last thing I did it was delete the value of magic cookie, in the first try it failed but in the second it works!,” Abdullah told The Hacker News. “The all value (title, description, tags) got change and I got redirected to my photos.”
The teen reported the vulnerability to Yahoo! and it was fixed in less than 12 hours by the Yahoo! security team. He got the reply from Yahoo! after more than a month and is still waiting for his bounty.
Reference- http://thehackernews.com/
No comments:
Post a Comment