Asset inventory and vulnerability management go hand in hand with IDS. Knowing the role, function, and vulnerabilities of your assets will add valuable context to your investigations. AlienVault Unified Security Management (USM) includes IDS integrated with asset discovery and vulnerability scanning so you can quickly get all the information you need to respond to incidents.
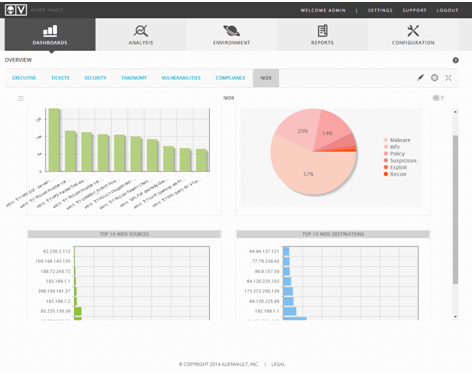
AlienVault’s Network IDS shows you the overall status of your network for a management view:
Best practices for Network IDS:
- Baselining or profiling normal network behavior is the first step for IDS deployment. Determining what’s “normal” for your network allows you to focus on anomalous and potentially malicious behavior. This saves you time and brings real threats to the surface quickly for remediation.
- Placement of the IDS device is an important consideration. Most often it is deployed behind the firewall on the edge of your network. This gives the highest visibility but it also excludes traffic that occurs between hosts. The right approach is determined by your available resources. Start with the most obvious placement of the device, then over time you can provide additional IDS focus into less obvious areas. You should also consider having multiple IDS installations to cover intra-host traffic
- You need to properly size your IDS installation by examining the amount of data that is flowing in BOTH directions where you wish to tap. Be sure to add overhead for future expansion.
- False positives occur when your IDS alerts you to a threat that you know is innocuous. An improperly tuned IDS will generate an overwhelming number of false positives. Establishing a policy that removes known false positives will save time in future investigations and prevent unwarranted escalations. Tuning your IDS to report as few false positives as possible will make your life much easier, as you can focus on the more important issues with the least distraction possible.
AlienVault USM reduces false positives through the fidelity of its correlation rules. The AlienVault research team has a deep understanding of the data sources entering the correlation engine. This insight allows them to create accurate correlation rules based on actual behavior seen in the wild, as opposed to just guessing what you *might* have integrated like other products have to do. Furthermore, when alarms do occur, USM provides the rich context needed to make the determination of validity. You can spend less time swiveling in your chair from console to console, and focus on the incident.
The Alarm Taxonomy view in AlienVault USM allows you to quickly determine the priority of your investigations. Spend less time wondering what a Conficker or HeartBleed is and more time investigating infections or exploits.
- The default settings for which files to watch are not enough. The defaults for HIDS usually only monitor changes to the basic operating system files. They may not have awareness of applications you have installed or proprietary data you wish to safeguard.
- Define what critical data resides on your assets and create policies to detect changes in that data
- If your company uses custom applications, be sure to include the logs for them in your HIDS configuration
- As with Network IDS, removing the occurrence of false positives is critical
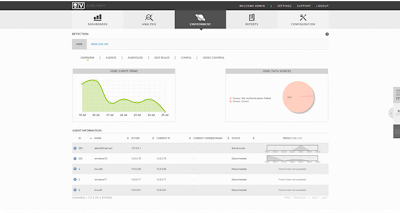
The AlienVault USM Host IDS overview screen, shows OSSEC agent information:
- Like physical network detection, placement of WIDS is also paramount. Make sure you are watching in the right places.
- Placement should be within the range of existing wireless signals
- Record and inventory existing Access Point names and whitelist them
When it comes to finding the threats in your environment, you need intrusion detection systems everywhere on your network. AlienVault Unified Security Management (USM) includes IDS fully integrated with asset discovery, vulnerability management, behavioral monitoring and Security Information and Event Management (SIEM) to tie it all together.
Learn more about AlienVault USM:
- Free 30-day trial
- Interactive test drive (no download required)
- 3-minute overview video
- On-demand product demo
Reference- http://thehackernews.com/


No comments:
Post a Comment