Back in June, Google first released Chrome 64-bit only in the browser’s Dev and Canary
Thursday, 28 August 2014
Google Chrome 64-bit Browser Finally Released As a Stable Version
Monday, 25 August 2014
Sony PlayStation Network Taken Down By DDoS Attack
It's possible that EVE Online and Guild Wars 2 have also been hit by the attackers. Developers on the EVE Online forums have announced DDoS issues, and many users on the Guild Wars
Sunday, 24 August 2014
Hacking Gmail App with 92 Percent Success Rate
Computer scientists the University of California Riverside Bourns College of Engineering and the University of Michigan have identified a new weakness they believe to exist in Android,
Facebook Awards $50,000 Under Its New 'Internet Defense Prize' Program
Till now, a number of large technology companies have bug bounty programs to reward researchers and cyber enthusiast who contribute in the security of Internet by finding out security holes in software or web platforms, and the social networking giant Facebook is the
Remote Attack Could Format Your Pebble Smartwatch Easily
Pebble Smartwatch, developed and released by Pebble Technology Corporation in 2013, is considered as one of the most popular SmartWatches that had become the most funded project in the history of Kickstarter. Just two hours after its crowd-funding campaign
Thursday, 21 August 2014
Hacking Traffic Lights is Amazingly Really Easy
The hacking scenes in hollywood movies has just been a source of entertainment for the technology industry, like we've seen traffic lights hacked in Die Hard and The Italian Job, but these movies always inspire hackers to perform similar hacking attacks in day-to-day life.
AlienVault Releases Intrusion Detection Systems (IDS) Best Practices
Monday, 18 August 2014
Hillary Clinton's Phone Intercepted by German intelligence Agency
After the allegations that the U.S. National Security Agency (NSA) not only conducted mass surveillance on German citizens, but also spied on German Chancellor Angela Merkel’s own personal mobile phone for years, surveillance has become a big issue for Germany. So big, that Germany itself started spying on U.S.
According to the reports came from the German media on Friday, the German foreign
Grocery Stores 'Supervalu' and 'Albertsons' Hacked for Credit Card Data
Albertson’s and SuperValu - Two nation’s most popular supermarket store chains announced last weekend that a data breach may have revealed the credit and debit card information of their customers at a number of grocery store locations in more than 18 states.
Minnesota-based Supervalu announced that an unknown number of its customers who used their payment cards in around 180 stores between June 22 and July 17 may have had payment card data compromised by attackers who gained access to the Supervalu computer
Wednesday, 6 August 2014
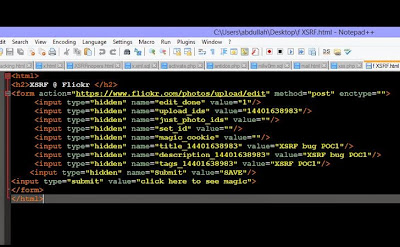
Flickr Cross-Site Request Forgery Vulnerability Patched
Flickr is one of the most popular photo sharing website with more than 87 million users, therefore some top major target for cybercriminals. The site was vulnerable to the most
Book — Unmasking the Social Engineer: The Human Element of Security
If we talk about old days, a hacker often rely on the natural helpfulness as well as weaknesses of people whom he wanted to target. This tactic to break into a computer network by gaining the confidence of an authorized user and get them to reveal information that compromises the network's security is known as Social Engineering.
WHAT IS SOCIAL ENGINEERING
Social engineering is nothing but a non technical kind of intrusion that relies heavily on
SandroRAT — Android Malware that Disguises itself as "Kaspersky Mobile Security" App
Researchers have warned users of Android devices to avoid app downloads from particularly unauthorized sources, since a new and sophisticated piece of malware is targeting Android users through phishing emails.
The malware, dubbed SandroRAT, is currently being used by cybercriminals to target Android users in Poland via a widely spread email spam campaign that delivers a new
Airplanes Can Be Hacked Through Wireless In-flight Entertainment System
Almost a year ago, at the ‘Hack In The Box’ security summit in Amsterdam, a security researcher at N.Runs and a commercial airline pilot, Hugo Teso presented a demonstration that it's possible to take control of aircraft flight systems and communications using an Android smartphone and some specialized attack code.
Quite similar to the previous one, a security researcher claims to have devised a method that
Jobvite Recruitment Service Website Vulnerable to Hackers
Jobvite, a recruiting platform for the social web, is found vulnerable to the most common, but critical web application vulnerabilities that could allow an attacker to compromise and steal the database of the company's website.
Jobvite is a Social recruiting and applicant tracking created for companies with the highest expectations of recruiting technology and candidate quality. Growing companies use
POWELIKS — A Persistent Windows Malware Without Any Installer File
Researchers dubbed this persistent malware as Poweliks, which resides in the computer
Thousands of Mozilla Developers Emails and Password Exposed Accidentally
The email addresses of over 76,000 members of its Developer Network, along with 4000 “salted” passwords were disclosed through a database glitch that may have been exploited
Sunday, 3 August 2014
Hurray! Unlocking Your Cell Phone is Officially Legal Again
President Barack Obama signed a bill into law Friday that aims to make it legal for consumers to “unlock” their cell phones in order to change their cell phone service providers without paying for a new phone.
The bill is known as the Unlocking Consumer Choice and Wireless Competition Act, which orders the U.S. Library of Congress (LoC) to allow cell phone owners to "unlock" their devices
Godzilla Hacker Takes Down Several Pakistani Government Websites
Indian hacker Godzilla claimed responsibility to hack into one of the main proxy server of the Pakistan Government, which is being used to manage all the government websites. Once
Anonymous Group Takes Down Mossad's Website Over Gaza Conflict
The hacktivist group Anonymous has reportedly taken down the official website of the Israeli intelligence agency Mossad against Israel’s military incursion in Gaza, which has resulted in hundreds of civilian casualties. The government of Israel has yet to comment on the Mossad hack attack.
The ‘Hacktivists’ were able to take down Mossad’s website in a Distributed Denial of Service (DDoS) attack early morning, claims a statement on one of the Anonymous hacker’s
Subscribe to:
Comments (Atom)