What if the encrypted files don’t exist in the first place for law enforcement to decrypt it? That’s the motive behind DroidStealth, a new Android encryption tool that not only protects sensitive data with obfuscation, but also hides its existence on your phone as if it has nothing to hide.
DroidStealth Android app has been developed by security researchers from Delft University of Technology in the Netherlands and would come as a windfall to both the privacy lovers and the cyber criminals.
STEALTH LOGIN MECHANISM
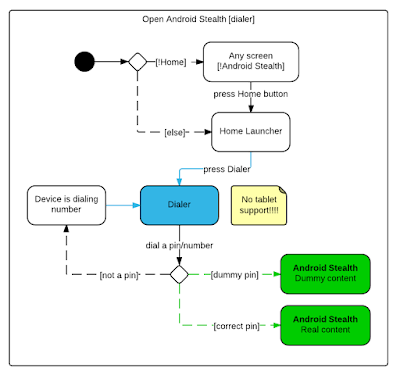
DroidStealth Android encryption tool creates a hidden folder in your phone in which it stores your all encrypted files. The app itself can be opened by simply dialing a phone number of any length which is actually a pin or by punching an invisible widget on your phone's home screen five times.
The application is developed in order to hide the existence of any protection mechanism that usually hints casual inspectors that they need to do some tampering in an attempt to gain access to users’ encrypted data.
According to developer quartet Olivier Hokke, Alex Kolpa, Joris van den Oever and Alex Walterbos of Delft University of Technology, several other disguise techniques, such as hiding the app within a flashlight program, are used to hide your private data.
"Since simply encrypting the data is not enough, our approach provides an added step of obfuscation that increases security of the data: DroidStealth hides itself," the group wrote in the paper titled, 'A Self-Compiling Android Data Obfuscation Tool' co-authored with supervisor Johan Pouwelse.
"Instead of actually calling the number, the application launches, requesting the pin code. Furthermore, DroidStealth fully intercepts the call, making sure the number never gets added to the call log."
FEATURES OF DROIDSTEALTH
- The app is stored in a secretive mode, and can be renamed to appear as a benign app to "hide in plain sight".
- The app doesn’t appear under the normal downloaded app list.
- The app provides notification to the user if any of the secret files are left unlocked.
- The can be kept out of the running process list when not in use.
- The app does not pop up in the recent visited list.
LIMITATIONS OF DROIDSTEALTH
In a centralized store the DroidStealth Android encryption tool would result in a possible exposure threat, so it was distributed "nomadically" as an untrusted Android application rather than from the Google Play Store which would show up in a user's list of installed apps.
Secret data files would be encrypted using Facebook's Conceal API and could not be accessed from other apps or from its original location.
DRAWBACK OF DROIDSTEALTH
This may be one of the major drawback of DroidStealth app among others, which are listed below:
- The data is encrypted and decrypted within the app.
- Uninstalling the app may lead to deletion of all the data.
- Low memory of the phone might lead to force quitting of the application and this might lead to loss of the data.
- If a user's phone gets in the hands of investigation while the app is under decode mode, then it would be difficult for them to secure the data from officials.
GET DROIDSTEALTH NOW
The developers said that the DroidStealth Android encryption tool's user interface (UI) is chosen black "in order to give users the feeling that they are indeed working in secret".
DroidStealth app is not released on Google Play, but users can get it with a untrusted APK version of the App. The APK is available as an unaligned version, while users can download the nomadic versions of the app that are available throughout the Internet.

No comments:
Post a Comment