Monday, 16 February 2015
Sunday, 15 February 2015
Hackers Stole $300 Million from 100 Banks Using Malware
Despite increased online and mobile banking security, banks are more often being targeted by hackers. A hacker group has infiltrated a number of banks and financial institutions in several countries, stealing hundreds of Millions of dollars in possibly the biggest bank heist the world has ever seen.
According to a report published by the New York Times on Saturday, hackers have stolen as much as $1 Billion from more than 100 banks and other financial companies in almost 30 nations, making it "the most sophisticated attack the world has seen to date."
In late 2013, banks in Russia, Japan, Europe, the United States and other countries fell victim to a massive, sophisticated malware hack that allowed the hackers to spy on bank officials in order to mimic their behavior, according to an upcoming report by Kaspersky Labs received by the NY Times.
DroidStealth — Android Encryption Tool with Stealth Capabilities
What if the encrypted files don’t exist in the first place for law enforcement to decrypt it? That’s the motive behind DroidStealth, a new Android encryption tool that not only protects sensitive data with obfuscation, but also hides its existence on your phone as if it has nothing to hide.
DroidStealth Android app has been developed by security researchers from Delft University of Technology in the Netherlands and would come as a windfall to both the privacy lovers and the cyber criminals.
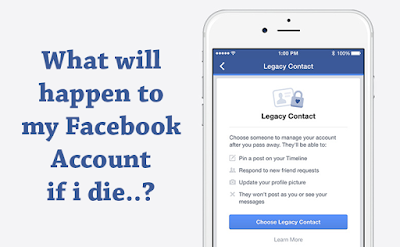
Facebook Legacy Contact — Control What Happens to Your Account When You Die
The social networking giant is giving its users control over what happens to their Facebook accounts when they die.
Until now, Facebook allowed people to turn the profiles of their loved one into "memorialized" accounts after Facebook verifies that person has died, meaning the account could be viewed but not be managed or edited. But Facebook is now adding a new option that users can select prior to their death: 'Legacy Contact'.
Saturday, 14 February 2015
Facebook launches ThreatExchange for Sharing Cyber Security Threats
Social Networking giant Facebook has just launched a new platform called ThreatExchange, which is designed to mount a coordinated defense against cybercrime.
Many security professionals rely largely on manual methods for collecting, analyzing, and consuming information about latest cyber security threats such as malware and botnets.
Whereas, Mark Zuckerberg’s ThreatExchange is a unique social media platform where multiple organizations can sign up and share information about new threats to cyber security, new types of hacks, phishing attacks and malicious activities they may have experienced.
Hackers Can Remotely Install Malware Apps to Your Android Device
Tod Beardsley, technical lead for the Metasploit Framework at Rapid7 warns that an X-Frame-Options (XFO) vulnerability – when combined with a recent Android WebView (Jelly Bean) flaw – creates a way for hackers to quietly install any arbitrary app from the Play store onto victims’ device even without the users consent.
Facebook Vulnerability Allows Hacker to Delete Any Photo Album
Security Researcher Laxman Muthiyah told The Hacker News that the vulnerability actually resides in Facebook Graph API mechanism, which allows "a hacker to delete any photo album on Facebook. Any photo album owned by an user or a page or a group could be deleted."
Subscribe to:
Comments (Atom)