Yes, Microsoft accidentally released a test patch (KB3877432) to consumer machines running Windows 7, making users believe that the Windows Update service got hacked, and they are infected with malware.
Thursday, 1 October 2015
Microsoft 'Accidentally' pushed 'Test patch' Update to All Windows 7 Users
Deadly Simple Exploit Bypasses Apple Gatekeeper Security to Install Malicious Apps
Patrick Wardle, director of research at security firm Synack, has found a deadly simple way that completely bypass one of the core security features in Mac OS X i.e. Gatekeeper.
TrueCrypt Encryption Software Has Two Critical Flaws: It's time to Move On
If you are among thousands of privacy-conscious people who are still using ‘no longer available’TrueCrypt Encryption Software, then you need to pay attention.
Two critical security vulnerabilities have been discovered in the most famous encryption tool, TrueCrypt, that could expose the user’s data to hackers if exploited.
Worse yet, TrueCrypt was audited earlier this by a team of Security researchers and found to be backdoor-free.
Wednesday, 30 September 2015
Microsoft Responds To Windows 10 Spying Concerns, But It will Still Collect Your Data
 |
After a number of controversial data mining features and privacy invasions within Microsoft's newest operating system, Microsoft finally broke the ice, almost two months since the launch of Windows 10.
Microsoft has finally responded to the growing privacy concerns around its new operating system to regain the trust of the users who are concerned about their online privacy related to Windows 10.
Monday, 16 February 2015
Sunday, 15 February 2015
Hackers Stole $300 Million from 100 Banks Using Malware
Despite increased online and mobile banking security, banks are more often being targeted by hackers. A hacker group has infiltrated a number of banks and financial institutions in several countries, stealing hundreds of Millions of dollars in possibly the biggest bank heist the world has ever seen.
According to a report published by the New York Times on Saturday, hackers have stolen as much as $1 Billion from more than 100 banks and other financial companies in almost 30 nations, making it "the most sophisticated attack the world has seen to date."
In late 2013, banks in Russia, Japan, Europe, the United States and other countries fell victim to a massive, sophisticated malware hack that allowed the hackers to spy on bank officials in order to mimic their behavior, according to an upcoming report by Kaspersky Labs received by the NY Times.
DroidStealth — Android Encryption Tool with Stealth Capabilities
What if the encrypted files don’t exist in the first place for law enforcement to decrypt it? That’s the motive behind DroidStealth, a new Android encryption tool that not only protects sensitive data with obfuscation, but also hides its existence on your phone as if it has nothing to hide.
DroidStealth Android app has been developed by security researchers from Delft University of Technology in the Netherlands and would come as a windfall to both the privacy lovers and the cyber criminals.
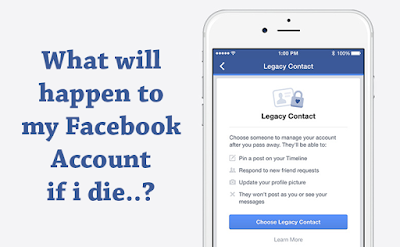
Facebook Legacy Contact — Control What Happens to Your Account When You Die
The social networking giant is giving its users control over what happens to their Facebook accounts when they die.
Until now, Facebook allowed people to turn the profiles of their loved one into "memorialized" accounts after Facebook verifies that person has died, meaning the account could be viewed but not be managed or edited. But Facebook is now adding a new option that users can select prior to their death: 'Legacy Contact'.
Saturday, 14 February 2015
Facebook launches ThreatExchange for Sharing Cyber Security Threats
Social Networking giant Facebook has just launched a new platform called ThreatExchange, which is designed to mount a coordinated defense against cybercrime.
Many security professionals rely largely on manual methods for collecting, analyzing, and consuming information about latest cyber security threats such as malware and botnets.
Whereas, Mark Zuckerberg’s ThreatExchange is a unique social media platform where multiple organizations can sign up and share information about new threats to cyber security, new types of hacks, phishing attacks and malicious activities they may have experienced.
Hackers Can Remotely Install Malware Apps to Your Android Device
Tod Beardsley, technical lead for the Metasploit Framework at Rapid7 warns that an X-Frame-Options (XFO) vulnerability – when combined with a recent Android WebView (Jelly Bean) flaw – creates a way for hackers to quietly install any arbitrary app from the Play store onto victims’ device even without the users consent.
Facebook Vulnerability Allows Hacker to Delete Any Photo Album
Security Researcher Laxman Muthiyah told The Hacker News that the vulnerability actually resides in Facebook Graph API mechanism, which allows "a hacker to delete any photo album on Facebook. Any photo album owned by an user or a page or a group could be deleted."
Wednesday, 28 January 2015
Links Found between NSA, Regin Spy tool and QWERTY Keylogger
REGIN MALWARE
"Regin" is a highly advanced, sophisticated piece of malware the researchers believe was developed by nation state to spy on a wide-range of international targets including governments, infrastructure operators and other high-profile individuals since at least 2008.
Regin was first discovered in November 2014 by the researchers at antivirus software maker Symantec and was said to be more sophisticated than both Stuxnet and Duqu.
The malware alleged to have been used against targets in Algeria, Afghanistan, Belgium, Brazil, Fiji, Germany, Iran, India, Indonesia, Kiribati, Malaysia, Pakistan, Russia and Syria, among others.
The recent evidence comes from the journalists at Der Spiegel who published the source code for a malicious program code-named 'QWERTY' – "a piece of software designed to surreptitiously intercept all keyboard keys pressed by the victim and record them for later inspection."
QWERTY KEYLOGGER MALWARE
The malicious program was revealed earlier this month when Der Spiegel magazine published a detailed article on the US National Security Agency's cyber espionage operations based on documents obtained from the former NSA contractor Edward Snowden.
The QWERTY program is included in the malware products used by the NSA and other intelligence agencies worldwide that are part of the Five Eyes Alliance (US, Australia, Canada, New Zealand and the United Kingdom) in order to eavesdrop and conduct destructive cyber operations on targets.
QWERTY = REGIN
After examining QWERTY’s code, the security analysts at Kaspersky Labs concluded that the keylogger’s source code can be linked to 'Regin,' and that the malware developers of QWERTY and Regin are either the same, or work closely together.
Moreover, the researchers also found that both QWERTY and the 50251 plug-in depend on a different module of the Regin platform identified as 50225 which relies on kernel hooking functions. This strongly proves that QWERTY can only operate as part of the Regin platform.
"Considering the extreme complexity of the Regin platform and little chance that it can be duplicated by somebody without having access to its sourcecodes, we conclude the QWERTY malware developers and the Regin developers are the same or working together," Costin Raiu and Igor Soumenkov, researchers at Kaspersky’s Securelist blog, said on Tuesday.
Der Spiegel reported that QWERTY is likely a plug-in of a unified malware framework codenamed WARRIORPRIDE that is been used by all Five Eye partners. Also, it is several years old and has likely already been replaced.
However, the link between QWERTY and Regin suggests that the cyber espionage malware platform, security researchers call Regin, is none other than WARRIORPRIDE.
Regin tool has also been linked to hacks which targeted the International Atomic Energy Agency based in Austria and the 2011 attack on European Commission computers, Spiegel said.
Refernce: http://thehackernews.com/2015/01/nsa-regin-qwerty-keylogger_27.html
Critical GHOST vulnerability affects most Linux Systems
The vulnerability, dubbed "GHOST" and assigned CVE-2015-0235, was discovered and disclosed by the security researchers from Redwood Shores, California-based security firm Qualys on Tuesday.
CRITICAL AS HEARTBLEED AND SHELLSHOCK
GHOST is considered to be critical because hackers could exploit it to silently gain complete control of a targeted Linux system without having any prior knowledge of system credentials (i.e. administrative passwords).
The flaw represents an immense Internet threat, in some ways similar to the Heartbleed, Shellshock andPoodle bugs that came to light last year.
WHY GHOST ?
The vulnerability in the GNU C Library (glibc) is dubbed GHOST because it can be triggered by the library'sgethostbyname family of functions. Glibc is a repository of open-source software written in the C and C++ coding languages that defines system calls.
The problem actual originates from a heap-based buffer overflow found in the __nss_hostname_digits_dots()function in glibc. This function is especially invoked by the _gethostbyname and gethostbyname2() function calls.
According to the researchers, a remote attacker has ability to call either of these functions which could allow them to exploit the vulnerability in an effort to execute arbitrary code with the permissions of the user running the application.
EXPLOIT CODE
In an attempt to highlight the severity of the risk, security researchers were able to write proof-of-concept exploit code that is capable to carry out a full-fledged remote code execution attack against the Exim mail server.
The researcher’s exploit able to bypass all existing exploit protections (like ASLR, PIE and NX) available on both 32-bit and 64-bit systems, including position independent executions, address space layout randomization and no execute protections.
Using the exploit, an attacker is able to craft malicious emails that could automatically compromise a vulnerable server without the email even being opened, according to Amol Sarwate, director of engineering with Qualys.
So far, the company has not published the exploit code to the public but eventually it plans to make the exploit available as a Metasploit module.
VERSIONS AFFECTED
The vulnerability affects versions of glibc as far back as glibc-2.2, which was released in 2000.
In addition to Exim mail server, server software vulnerable to GHOST includes Apache, Exim, Sendmail, Nginx, MySQL, CUPS, Samba and many others, according to a later post by Qualys researchers on the Full Disclosure mailing list.
"Unfortunately, it was not recognized as a security threat; as a result, most stable and long-term-support distributions were left exposed (and still are): Debian 7 (wheezy), Red Hat Enterprise Linux 6 & 7, CentOS 6 & 7, Ubuntu 12.04, for example," researchers from Qualys said in an advisory published Tuesday.
FIXES AVAILABLE FOR SOME LINUX DISTRIBUTIONS
However, major distributors of the Linux operating system, including Red Hat, Debian and Ubuntu, updated their software on Tuesday to thwart the serious cyber threat. In order to update systems, core functions or the entire affected server reboot is required.
Red Hat, the No. 1 provider of Linux software to businesses, recommends its customers to update their systems "as soon as possible to mitigate any potential risk."
Refrence: http://thehackernews.com/2015/01/ghost-linux-security-vulnerability27.html
Taylor Swift's Twitter and Instagram Accounts Hacked
The very popular Pop star Taylor Swift became the latest celebrity to have their social media accounts hacked on Tuesday.
The 25-year-old "Shake It Off" singer, who has the fourth-most popular Twitter account with 51.4 million followers, appeared to be asking her millions of followers to follow @veriuser and @lizzard.
Swift confirmed that her Twitter and Instagram accounts were hacked on Tuesday afternoon, and also that the rogue posts were quickly removed from the social media websites.
"My Twitter got hacked but don't worry, Twitter is deleting the hacker tweets and locking my account until they can figure out how this happened and get me new passwords," said a statement posted on Swift's personal Tumblr page.
The accounts were taken for just 15 minutes, but when it belongs to Taylor Swift, that makes it a big hit. At the time, a Tweet went out from @TaylorSwift13 to her millions of fans, saying, "go follow my boy, @lizzard :)"
Yes Lizzards are the same guys who recently took down Sony's PlayStation game networks, among other things, as @lizzard profile claimed to be the "Leader of Lizard Squad" — the hacking group that's ostensibly behind this attack.
The hackers not only took over her social media accounts, but also threatened Taylor Swift to release here nude pictures, on which the pop star says "none existed."
"Any hackers saying they have 'nudes'?" Swift tweeted after retaking control of her Twitter account. "Psssh you'd love that wouldn't you! Have fun photo-shopping cause you got NOTHING."
An Instagram photo sent out from Swift's account with over 20 million followers urged her fans to follow another user supposedly involved in the Twitter hack.
Both the Instagram photo and the rogue Tweets from her accounts have vanished. However, @lizzard and @veriuser's Twitter accounts have been suspended by Twitter.
Swift even mimicked the lyrics to her hit "Shake It Off" by tweeting, "Cause the hackers gonna hack, hack, hack, hack, hack ..."
Though, hacking the fourth largest profile on Twitter makes the hack one of the higher-profile breaches that has occurred on the network.
Refrence: http://thehackernews.com/2015/01/taylor-swift-twitter-instagram-hacked.html
Subscribe to:
Comments (Atom)