Simplocker (Android/Simplocker.A) is the latest Android ransomware that has ability to encrypt the files using Advanced Encryption Standard (AES) on the Android device SD cards demanding users pay a ransom of 260 UAH (Ukrainian hryvnias), which is roughly equal to $21 US, for those files to be decrypted.
To hide their track, the malware author is using the Command-and-Control server hosted on TOR .onion domain, which makes it difficult to trace the server's physical location or determine who is operating it.
The malware collects information about the users’ phone such as IMEI number, Operating System, phone model and manufacturer to send it all to Command-and-Control server.
STUDENT CRACKS SIMPLOCKER RANSOMWARE
Now, an undergraduate student Simon Bell from the University of Sussex promises to release a Java application to decrypt the files encrypted by the so-called first Android File-encrypting and TOR-enabled Mobile Ransomware.
In a technical blog, Secure Honey published Monday, the student has given a detailed explanation on how to reverse Simplocker Ransomware and develop an app to pluck the decryption keys stored within.
"This dissection shows how the app encrypts user's files and that information about the phone is sent to a C&C (command and control) server on the TOR network," Bell writes. "But one important question remains unanswered: would it be possible to decrypt files that have been encrypted by the app without connecting to the C&C server? In other words: can we reverse the damage done by this app?"
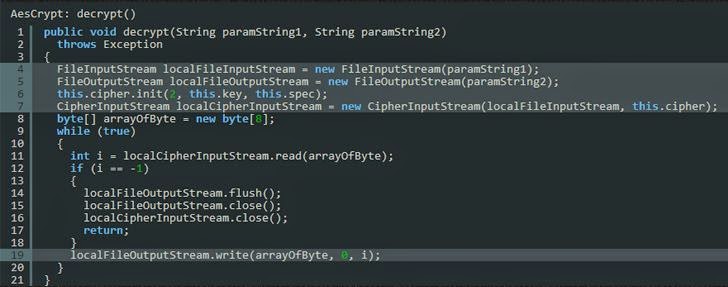
Bell detailed the Static and Dynamic analysis of the Ransomware code and found a method called decrypt() which is very similar to the encrypt() method.
“Obviously this method carries out the decryption on the input file and produces the decrypted output file,” he said. “The same line numbers from the encrypt() method are highlighted to demonstrate how decryption occurs.”
In his next blog, he’ll publish the crypto-cracking app allowing victims to free their devices from the nasty Ransomware without paying any ransom fine.
We have seen many similar threat such as CryptoLocker, CryptoWall and PrisonLocker ransomware targeting users Worldwide, but the only difference is that first they were targeting PCs and now with the popularity of Android platform, they are targeting Smartphones.
We have seen many similar threat such as CryptoLocker, CryptoWall and PrisonLocker ransomware targeting users Worldwide, but the only difference is that first they were targeting PCs and now with the popularity of Android platform, they are targeting Smartphones.
But to keep yourself away from such emerging threats, it is always important for you to keep the back-up of all your files either manually on the computer system or with the use of cloud backup services like Dropbox, Google drive etc.
We'll update you the antidote for this ransomware as soon as he get it done. Stay Tuned!
Reference- http://thehackernews.com/


No comments:
Post a Comment