Monday, 30 June 2014
Movie Review: The Internet’s Own Boy - The story of Aaron Swartz
Disqus Wordpress Plugin Flaw Leaves Millions of Blogs Vulnerable to Hackers
While there are more than 70 million websites on the Internet currently running WordPress, about 1.3 million of them use the ‘Disqus Comment System’ Plugin, making it one of the
Sunday, 29 June 2014
'Tails' Operating System Website Has Been Hacked
Tails is a Linux-based highly secure Operating System, specially designed and optimized to preserve users' anonymity and privacy. Hacker, who named himself "Sum guy", managed to
Saturday, 28 June 2014
Tracy Morgan Dead? Facebook Scam Targeting Users with Malware
Another Facebook scam is circulating across the social networking website just a day before the former “Saturday Night Live” and “30 Rock” star Tracy Morgan was critically hurt in a six-vehicle fatal accident on the New Jersey Turnpike that killed his friend and writer 62-year-old James McNair.
New Banking Malware with Network Sniffer Spreading Rapidly Worldwide
Until now, we have seen banking Trojans affecting the infected device and steal users’ financial credentials in order to run them out of their money. But nowadays, malware authors are adopting more sophisticated techniques in an effort to target as many victims as they can.
Friday, 27 June 2014
20-Year Old Vulnerability in LZO Compression Algorithm Went to Planet Mars
Lempel-Ziv-Oberhumer (LZO) was developed in 1994 by Markus Oberhumer and currently it is one of the most popular and widespread compression algorithm used in the Linux kernel, some Samsung Android mobile devices, other embedded devices and several open-source libraries including OpenVPN, MPlayer2, Libav, FFmpeg.
Android 4.3 and Earlier versions Vulnerable to Critical Code-Execution Flaw
A critical code-execution vulnerability almost affecting everyone those are not running the most updated version of Google Android, i.e. Android version 4.4 also known as KitKat.
After nine months of vulnerability disclosure to the Android security team, researchers of the Application Security team at IBM have finally revealed all the possible details of a serious code-execution vulnerability that still affects the Android devices running versions 4.3 and
Thursday, 26 June 2014
FIFA World Cup Security Team Accidentally Reveals their Wi-Fi Password
This FIFA World Cup,the security has been really going well and yet no calamitous incident reported so far, other than the security company who is responsible to keep an eye on the event’s security, itself tweeted a photograph of their state-of-the-art monitoring centre that exposed the World Cup security centre's internal Wi-Fi password to the whole world.
Stuxnet-like 'Havex' Malware Strikes European SCADA Systems
Just like Famous Stuxnet Worm, which was specially designed to sabotage the Iranian nuclear project, the new trojan Havex is also programmed to infect industrial control system softwares of SCADA and ICS systems, with the capability to possibly disable hydroelectric dams, overload nuclear power plants, and even can shut down a country’s power grid with a single keystroke.
Zero-Day TimThumb WebShot Vulnerability leaves Thousands of Wordpress Blogs at Risk
Yesterday we learned of a critical Zero-day vulnerability in a popular image resizing library called TimThumb, which is used in thousands WordPress themes and plugins.
WordPress is a free and open source blogging tool and a content management system (CMS) with more than 30,000 plugins, each of which offers custom functions and features enabling users to tailor their sites to their specific needs, therefore it is easy to setup and use, that’s why tens of millions of websites across the world opt it.
Wednesday, 25 June 2014
How To Jailbreak iOS 7.1 And 7.1.1 Untethered Using 'Pangu' Jailbreak Tool
This untethered jailbreak is compatible with iPhone 5s, iPhone 5c, iPhone 4S, iPhone 4, iPad Air, iPad 4, iPad 3, iPad 2, iPad mini, Retina iPad mini and iPod touch 5G running iOS 7.1-iOS 7.1.1.
BBC News iOS App Not Hacked, Breaking News Push Messages Sent in Error
If you are one of the users of the BBC News iPhone app, then you might have receive a strange message as a breaking news notification earlier this morning.
The message was sent on two separate time durations. First the message reads: "NYPD Twitter campaign 'backfires' after hashtag hijacked," then strangely adds: "Push sucks! Pull blows!"
Researchers Uncover Spying Tool Used by Governments to Hijack all Types of Smartphones
Researchers from the Citizen Lab at the Munk School of Global Affairs at the University of Toronto and computer security firm Kaspersky Lab have unearthed a broad network of controversial spyware which is specially designed to give law enforcement agencies complete access to a suspect's phone for the purpose of surveillance.
India to Host 3rd Annual 'The Hackers Conference' this Year in August
A crowd of Cyberspace experts along with the best minds in Indian hacking community, leaders in the information security community, policymakers and Government representatives will come together at a common platform to join their efforts in addressing the most critical issues of the Internet Cyberspace.
Tuesday, 24 June 2014
Intel Developing RFID Tracking and Remote Controlled 'Kill Switch' for Laptops
Kill Switch - the ability to render devices non-operational to prevent theft - has become a hot topic nowadays. The ability to remotely destroy data of the device lost or stolen has been available for quite some time now, but Kill switch not only remotely destroy the devices’ data but also the device itself, making it useless for the thieves.
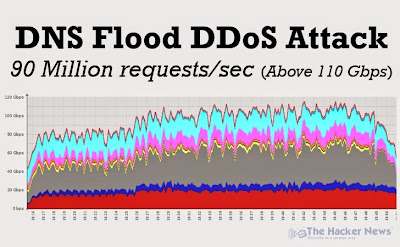
DNS Flood DDoS Attack Hit Video Gaming Industry with 90 Million Requests per Second
Hackers are leveraging large number of compromised machines (a botnet network) to carry out massive DNS Flood DDoS attack against a large Video Gaming Industry website, peaking above 110 Gbps.
A US based security solutions provider Incapsula, is protecting a famous Video Gaming website from this high bandwidth DDoS attack from last 48 Hours and according to them, the attack is still continuing. Incapsula has not yet disclosed the name of the video gaming company.
“The attack is still going on - that over 48 hours by now, from what I see it ain't gonna stop anytime soon,” Incapsula spokesperson wrote in an e-mail to The Hacker News.
DDoS AT 90 MILLION PACKETS/SECOND
The researchers at the security firm noticed a surge of massive DNS Flood DDoS attack on one of its clients, peaking at approximately 90 Mpps (Million Packets Per Second), which is really a very very big number. Majority number of attacking IP addresses belong to China and India. “Good reason to think many are spoofed.” Incapsula told THN.
The hackers used a more evil DDoS practice, the DNS flood attack, which is completely different and more responsive from the previously most commonly used DNS amplification attack, both in their methods of execution and in the type of grief they aim to deliver.
On one side, where DNS amplification attack is an asymmetrical DDoS attack, in which an attacker set the source address to that of the targeted victim by using spoofed Internet Protocol (IP) of the target, which means the target receives the replies from all the DNS servers that are used, making it the recipient of much larger DNS responses.
DNS FLOOD WITHOUT AMPLIFICATION
On the other side, DNS floods attacks are symmetrical DDoS attacks that works by sending thousands of rapid valid DNS requests to the targeted server, thereby giving the server more traffic than it can handle resulting in slower and slower response times for legitimate requests.
DNS servers provide the roadmap to the Internet, and help clients find the servers they are looking for, but a DNS floods attempt to exhaust server-side assets (for e.g., memory or CPU) with the large number of UDP requests generated by the malicious scripts running on several compromised botnet machines. The packets sends per seconds are even larger in this case compare to DNS amplification attack.
Currently researchers at the DDoS protection service are mitigating with this attack with just one of their servers, that can process upto 170Gbps/100Mpps worth of traffic at an inline rate.
Until now, we have seen 50-60Gbps DNS Flood DDoS attack without amplification, but reaching above 110Gbps seems that hackers are making their comeback in really a very big way.
As we all have seen that DDoS trend is changing and to perform massive DDoS attacks, hacker are using every tantrum by leveraging the weakness of system applications to compromise them in order to boost the size of their botnet network.
Reference- http://thehackernews.com/
Monday, 23 June 2014
Open Wireless Router Let You Share Your Internet with the World
In this era of mass surveillance, we have always learned from security folks to protect and encrypt our communication and networks, especially widely open private Wi-Fi networks.
It is always recommended to use a strong password and encryption on Wireless Routers in an effort to safeguard the privacy and security of our web communication and personal data.
Quite the contrary, a group of activists says opening up your home Wi-Fi network could not only enhance your privacy, but actually increase it in the process.
Cisco Open Sources Experimental Small Domain Block Cipher
Block cipher encrypts Plain-text to Cipher-text by applying cryptographic key and algorithm to a block of data at once as a group rather than to one bit at a time, so that identical blocks of text do not get encrypted the same way.
However, some applications need smaller blocks, and possibly non-binary blocks. So, to fulfil this need Cisco is providing a small block cipher, what it calls “FNR” (Flexible Naor and Reingold), but currently it is an experimental block cipher rather a production software.
Sashank Dara, software engineer at the security technology group Cisco, says in a detailed explanation that FNR is a flexible length small domain block cipher for encrypting objects that works without the need for padding, as happens in the traditional block ciphers such as AES (Advanced Encryption Standard) and DES (Data Encryption Standard).
“But one of the issues is the need for padding—so if you need to encrypt small amounts of data you may end with a huge difference in input vs. output size. As an example, using AES/128 on ECB mode to encrypt an IPv4 address results in an input size of 32 bits, but an output size of 128 bits. This may not be desired for some applications.” Sashank Dara said.
FEATURES OF FNR
- Format-preserving encryption (FPE) - the length of plaintext and ciphertext remains same.
- FNR is flexible for large input domains that are greater than 32 bits and less than 128 bits.
- The encryption key length is not dependent on the input length and rather depends on underlying pseudo-random function (PRF).
I have taken an example from Wikipedia to explain the importance of Format-preserving encryption (FPE):
Suppose we want to encrypt a 16-digit credit card number 1234567812345670 using AES algorithm like ECB or CBC that will transform a credit card number into a large, fixed-length, binary value i.e. hexadecimal output value - 0x96a45cbcf9c2a9425cde9e274948cb67, which contains many bytes that are considered invalid when compared to a typical credit card number. If a credit card number is stored in a column of a database whose entries are char or varchar data, then the encrypted data cannot be stored in same column without changing the format of the column. If the encrypted data is Base64 encoded to ensure that it only contains valid characters, the size of the encrypted credit card number increases from 16 bytes to 24 bytes, changing the encrypted credit card number to lqRcvPnCqUJc3p4nSUjLZw==. In either case, applications that process the credit number may similarly be unable to handle an encrypted value without some modification.
SMALL-BLOCK ENCRYPTION SECURITY?
Small domain block ciphers are useful tool in designing privacy of sensitive data fields of smaller length, but smaller blocks leads to important security issues and building a secure small block cipher is known to be a tricky task.
According to Cisco, FNR is an experimental small domain block cipher for encrypting objects like IPv4, Port numbers, MAC Addresses, IPv6 address and any random short strings and numbers, while preserving their input length.
“Like all deterministic encryption methods, this does not provide semantic security, but determinism is needed in situations where anonymizing telemetry and log data (especially in cloud based network monitoring scenarios) is necessary,” Cisco warned.
Cisco has Open Sourced the FNR encryption scheme under open source license LGPLv2 on Github.
Cisco has Open Sourced the FNR encryption scheme under open source license LGPLv2 on Github.
Reference- http://thehackernews.com/
Largest DDoS Attack Hit Hong Kong Democracy Voting Website
Hackers and cyber attacks are getting evil and worst nightmare for companies day-by-day. Just last week a group of hackers ruined the code-hosting and software collaboration platform, ‘Code Spaces’ by destroying their Amazon cloud server, complete data and its backup files too.
Recently, the largest ever and most severe Distributed Denial of Service (DDoS) attacks in the history of the Internet has been recorded that hit the online democracy poll promoting opinion on the upcoming Hong Kong elections.
PopVote, an online mock election operated by The University of Hong Kong’s Public Opinion Program, by Saturday recorded more than half a million votes in less than 30 hours in the unofficial referendum that provided permanent residents of Hong Kong to choose their preferred political representatives, that is suppose to be continued until June 29.
However, the Chief Executive is officially chosen by a 1,200-member Election Committee under the current political system and drawn largely from pro-Beijing and business camps.
On the first day of voting, China’s State Council denounced the voting as “illegal and invalid.” Hong Kong’s chief executive, Leung Chun-ying, said all the proposals on the ballot are not complied with Hong Kong’s Basic Law, the territory’s de facto constitution.
On Friday, Matthew Prince, the CEO and co-founder of San Francisco based CloudFlare, the web performance company maintaining the voting website, said that the DDoS attack on the Occupy Central’s voting platform was “one of the largest and most persistent” ever.
According to Prince, the cybercriminals appeared to be using a network of compromised computers around the world to effectively disable the service of the voting website with an overwhelming amount of traffic. In such cases of attacks, the computer users who are exploited are usually unaware that their systems have been compromised.
Prince also wrote on Twitter: “Battling 300Gbps+ attack right now,” on the first day that the vote began. Three hundred gigabits per second is an enormous amount of data to take down any huge servers.
Also a DDoS attack last year on Spamhaus, a non-profit organisation that aims to help email providers filter out spams and other unwanted contents, is largely considered to be the biggest DDoS attack in the history, which the Cloudflare said the attack “almost broke the Internet.”
Reference- http://thehackernews.com/
Sunday, 22 June 2014
Google Unveils BoringSSL, Another Flavor of OpenSSL
The open source encryption protocol, OpenSSL, which is used by several social networks, search engines, banks and other websites to enable secure connections while transmitting data, came to everybody's attention following the Heartbleed vulnerability, a critical bug in the OpenSSL's implementation of the TLS/DTLS heartbeat extension that allows attackers to read portions of the affected server’s memory, potentially revealing users data, that the server did not intend to reveal.
Now, the biggest Internet giant Google is launching a new fork of OpenSSL, which they dubbed asBoringSSL, developed by its own independent work with the code.
"We have used a number of patches on top of OpenSSL for many years," Adam Langley, a cryptography engineer and Google employee, wrote in a blog post introducing BoringSSL. "Some of them have been accepted into the main OpenSSL repository, but many of them don't mesh with OpenSSL's guarantee of API and ABI stability and many of them are a little too experimental."
So, from now on, the websites have three choices from three separate versions of OpenSSL to implement the secure socket layer and transport layer security protocols in order to enable secure connections while transmitting data.
Till now, Google makes use of its modified version of OpenSSL in its different products such as Chrome, Android, and various other things, that has been substantially rewritten and audited for potential security vulnerabilities.
But, now in an effort to integrate its code into a single and consistent library and to handle its massive amount of in-house patches, Google is releasing BoringSSL that can be easily distributed across many of its independent projects.
"But we’ll also be more able to import changes from LibreSSL and they are welcome to take changes from us," said Langley. "We have already relicensed some of our prior contributions to OpenSSL under an ISC license at their request and completely new code that we write will also be so licensed."
A few weeks after the terror of Heartbleed bug, the developers of OpenBSD operating system took initiative and announced LibreSSL under its new project Theo de Raadt. The OpenBSD project aims to provide a more trustworthy platform.
Along with its own fork of OpenSSL, Google will continue to contribute the OpenBSD foundation and the Core Infrastructure Initiative, which is at least $100,000 a year for at least three years in funding to OpenSSL developers so that they can improve OpenSSL’s badly written code base.
According to the blog post, BoringSSL is developed in such a way that strips out a number of Application Programing Interfaces (APIs) and Application Binary Interfaces (ABIs), and will change a much of its current code so that it's more readable and easier to maintain.
"There are no guarantees of API or ABI stability with this code: we are not aiming to replace OpenSSL as an open-source project," he wrote. "We will still be sending them bug fixes when we find them and we will be importing changes from upstream. Also, we will still be funding the Core Infrastructure Initiative and the OpenBSD Foundation."
This is really a good initiative taken by Google to build a strong community by putting up an enough of its initial efforts to get the ball rolling.
"We know you all want this tomorrow," the project's homepage states. "We are working as fast as we can but our primary focus is good software that we trust to run ourselves. We don't want to break your heart."
Reference- http://thehackernews.com/
Saturday, 21 June 2014
Cyber Attack On 'Code Spaces' Puts Hosting Service Out of Business
Code Spaces, a code-hosting and software collaboration platform used by different organizations for project management and development needs, was forced to shut down operations after an attacker compromised its internal system and deleted its customer’s data and backups as well.
This is really a nightmare for the code-hosting company based in Coventry, UK that claimed to offer "Rock Solid, Secure and Affordable Svn Hosting, Git Hosting and Project Management." Codespaces.com homepage shows a lengthy explanation on the attack and an apology from its customer.
“Code Spaces will not be able to operate beyond this point, the cost of resolving this issue to date and the expected cost of refunding customers who have been left without the service they paid for will put Code Spaces in an irreversible position both financially and in terms of ongoing credibility,” read the note. “As such at this point in time we have no alternative but to cease trading and concentrate on supporting our affected customers in exporting any remaining data they have left with us.”
The devastating security breach began with a Distributed Denial of Service (DDoS) attack over a period of 12 hours on 17 June followed by an attempt to extort money from the company.
The attacker also had gained unauthorized access to the control panel for the company's Amazon Web Service account (AWS) Elastic Compute Cloud (EC2) console and left extortion demands for the company officials along with a Hotmail address they were supposed to use to contact the attackers.
"Reaching out to the [email] address started a chain of events that revolved around the person trying to extort a large fee in order to resolve the DDoS," the company said on its homepage.
“Upon realization that somebody had access to our control panel, we started to investigate how access had been gained and what access that person had to the data in our systems,” Code Spaces said. “It became clear that so far no machine access had been achieved due to the intruder not having our private keys.”
The company changed its EC2 passwords, but when the system admins attempted to regain control of the system, and once recovery attempts were noticed, the hackers started deleting all the company's data, backups, machine configurations and off-site backups from the panel, leaving the company’s website unable to operate.
“We finally managed to get our panel access back, but not before he had removed all EBS snapshots, S3 buckets, all AMI’s, some EBS instances and several machine instances,” Code Spaces said. “In summary, most of our data, backups, machine configurations and offsite backups were either partially or completely deleted.”
The code-hosting website said it is now working to recover whatever data may be left so that customers can regain access to their files and migrate the remaining data to other services. All Git repositories and some svn nodes are available for export, although their backups and snapshots have been completely deleted.
Most of Code Spaces' Apache Subversion repositories and all Elastic Block Store (EBS) hosted database files and all virtual machines have also been erased, along with their backups and snapshots.
"Backing up data is one thing, but it is meaningless without a recovery plan, not only that [but also] a recovery plan—and one that is well-practiced and proven to work time and time again," the cache stated. "Code Spaces has a full recovery plan that has been proven to work and is, in fact, practiced."
After Ransomware such as CryptoLocker and CryptoWall, DDoS attacks have now become new trend for cybercriminals to extort a large amount by targeting various big and reputed companies.
Few days back, the popular RSS feed, Feedly and the note-taking and archiving site, Evernote also faced the same kind of attack and were briefly forced by the hackers to pay a ransom and luckily both the companies soon recovered from the attack. But, Code Spaces wasn’t so lucky. This is really a scarier incident in company’s life.
Reference- http://thehackernews.com/
Friday, 20 June 2014
Thursday, 19 June 2014
Millions of LinkedIn Users at Risk of Man-in-the-Middle Attack
Wednesday, 18 June 2014
20-years-old Alleged "NullCrew" Hacker Arrested by the FBI
The FBI officers have arrested a 20-year-old Tennessee man and charged with federal computer hacking for allegedly conspiring to launch cyber attacks on five organizations in 2013, including two universities and three companies in the US and Canada, federal law enforcement officials announced today.
Towelroot : One-Click Android Rooting Tool Released By Geohot
Geohot (aka George Hotz) - a famed cracker who was responsible for hacking the PlayStation 3 and subsequently being sued by Sony - has built and released a root tool called Towelroot on Sunday night that will let most Android smartphones users to root their Android device with one click only, as long as it has an unpatched version of the Linux kernel.
EXPLOITS LINUX KERNEL VULNERABILITY
Towelroot application exploits the same vulnerability (CVE-2014-3153) which was recently disclosed by the hacker Pinkie Pie in the Linux kernel version 3.14.5 and most versions of other Android devices, which could be leveraged by hackers to potentially acquire root access on affected devices.
Having root access of your device simply means you make System-level changes to your device such as accessing and modifying any file or program using any mode (single- or multi-user). It is just like operating an administrator account on a computer.
SUPPORTED DEVICES
Towelroot supports handful of devices so far including some particularly tough phones. here’s the list:
- AT&T Galaxy S5
- Verizon Galaxy S5
- Galaxy S4 Active
- Nexus 5
- AT&T Galaxy Note 3
- Verizon Galaxy Note 3
- Also some users have even reported its success with the all time favorite company of GeoHot, Sony Xperia SP C5303.
Geohot became famous for being the first person to carrier unlock the original iPhone in 2007 and later for creating the limera1n jailbreak tool for future versions of the iPhone. He gained fame after subsequently hacking the software of the PlayStation 3 console, thereby opening up the ability to add homebrew and play pirated games, for which he was taken to court by Sony.
HOW TO ROOT ANDROID DEVICE
Step 1: Download Android Rooting application from towelroot.com and install it.
Step 2: While Installation you might receive warning message saying that Towelroot "contains code that attempts to bypass Android's security". Just hit Install anyway after selecting the checkbox: "I understand and still want to install it".
Step 3: Once the Towelroot installation completes, launch the application and click the button reading "make it ra1n" and it will force your device to reboot.
Step 4: After the device reboots to home screen your phone will be rooted with its bootloader unlocked. Cheers!
Step 2: While Installation you might receive warning message saying that Towelroot "contains code that attempts to bypass Android's security". Just hit Install anyway after selecting the checkbox: "I understand and still want to install it".
Step 3: Once the Towelroot installation completes, launch the application and click the button reading "make it ra1n" and it will force your device to reboot.
Step 4: After the device reboots to home screen your phone will be rooted with its bootloader unlocked. Cheers!
Along with the Android users who were itching to get Android rooting technique for their devices and doing tons of things such as customizations, patching apps and installing third-party ROMs, the new tool will also allow cybercriminals as well to gain administrative access to a victim’s phone.
Specifically, at the same time the cyber criminal with the administrative access could potentially run malicious code, retrieve files, bypass third-party or security applications including containers like Samsung’s secure Knox sub-operating system, and place backdoors for future access on users’ devices.
$18000 BOUNTY GOES TO GEOHOT OR PINKIE PIE?
Till now, the developer edition of Samsung Galaxy S5 for Verizon and At&T have not receive root, for the reason XDA members started up a Crowd funded Bounty program, now valued at over $18,000, for achieving the root on Verizon and AT&T Samsung Galaxy S5 devices.
So, now the question is Who gonna fetch this raised bounty by XDA developers? On one hand, where the famed developer George Hotz (GeoHot) have developed the tool to root Samsung Galaxy S5 (Verizon and AT&T) and other Android devices, on the other hand Pinkie Pie have discovered the vulnerability exploited in the rooting tool, TowelRoot by GeoHot.
Reference- http://thehackernews.com/
Subscribe to:
Comments (Atom)